Release Notes¶
The following documentation provides release notes for individual versions of the Bowtie software. Release notes are broken down by the type of package (such as Client or Controller) and further grouped by type (such as bugfixes or features).
While we strive to provide complete release notes for updates, please be aware that these changes may not cover 100% of the changes included in a given release.
If you are looking for the latest version of a particular package, please rely on https://api.bowtie.works/ as the canonical source for latest updates.
Feeds¶
Release notes are also provided as RSS and Atom feeds:
Release History¶
26.02.003¶
Released on 25 February, 2026.
Meta Control Plane¶
Features¶
The platforms download page on api.bowtie.works has been redesigned to prominently display organization-specific custom packages in a recommended card, reducing the chance of accidentally downloading generic installers. Generic packages are now collapsed behind a toggle.
Bowtie-Cli¶
Features¶
A new
bowtie-ctl digcommand provides terminal-based DNS query evaluation, showing how Bowtie would handle a given domain lookup including disposition, upstream records, and response code. This mirrors the DNS Query Evaluator available in the Help UI and is useful for diagnostics over SSH or in scripted workflows.
Client¶
Fixes¶
The controller address input now automatically normalizes entries by prepending
https://when no protocol is specified, upgradinghttp://tohttps://, and stripping extraneous paths or parameters. This prevents configuration errors from mistyped or partially entered URLs.Fixed an issue where redeploying a controller could leave a stale peer behind, causing persistent “Unhealthy peers detected” warnings and route calculation errors. Stale controller-sourced peers are now automatically pruned.
26.02.002¶
Released on 19 February, 2026.
Server¶
Fixes¶
Fixed an issue that could prevent normal
sshbased logins from succeeding in GCE environments.Serial console access on Google Compute Engine is now interactive.
The base NixOS 25.11 has been updated to 2026-02-16 to pull in an updated openssl library.
26.02.001¶
Released on 17 February, 2026.
Server¶
Fixes¶
Fixed an issue where fresh controller deployments experienced a 2-minute delay before SSH connections could be established.
Features¶
Administrators can use patterns to override matches in block lists while keeping the rest of the block list in effect. There are two syntaxes available: *.example.com will allow only subdomains at the level specified and .example.com will allow all subdomains of example.com regardless of depth. Exact-match overrides continue to work as before.
Site ranges can now reference a Collection of CIDRs instead of requiring individually specified ranges. This allows administrators to maintain a shared set of network ranges across multiple sites, simplifying management of overlapping or repeated address space.
Client¶
Features¶
A new client configuration option,
enforce_block_list_while_paused, allows DNS block list enforcement to remain active while Bowtie is paused.When enabled, pausing the client no longer disables DNS block list filtering.
The client Help page has been redesigned with a new card-based dashboard layout.
Fixes¶
MacOS: In versions 26.01.002 and prior, a tunnel exclusion triggered by a WAN IP rule may fail to be removed when the WAN IP changes away from the rule.
Fixed an issue where the Bowtie client could not communicate with its background service in some MDM-managed macOS environments. The IPC socket has been moved to a universally accessible location.
26.01.002¶
Released on 27 January, 2026.
Client¶
Fixes¶
Improve performance by adding indexes to a number of key tables.
26.01.001¶
Important
This release includes important changes that administrators should review.Released on 22 January, 2026.
Server¶
Enhancements¶
Controllers will now capture and report the client source address when API keys are used.
The foundational operating system for Controllers has been updated from NixOS 25.05 to 25.11.
This update includes the following noteworthy version changes. If you rely on any of these packages for downstream integrations (such as observability with Grafana and Loki), ensure that the updated versions are compatible with your existing configuration (and update those configurations if necessary).
Package
Old Version
New Version
Linux kernel
6.1.158
6.1.159
dex2.42.0
2.44.0
grafana12.0.6
12.3.1
loki3.4.5
3.6.3
prometheus3.5.0
3.7.2
python3.12.12
3.13.9
tempo2.7.2
2.9.0
At time of writing, a scan of all operating system dependencies yielded no outstanding critical vulnerabilities requiring immediate action.
Upstream changes to configuration defaults that may impact Controllers include:
Grafana no longer reports third-party telemetry by default.
Deprecations¶
The “Minimum Peers Behavior” setting released in 25.02.001 has been deprecated since a separate, less-disruptive mechanism for automatic recovery from network partitions has been implemented. The setting is now disabled and cannot be reenabled, and has been removed from the Controller settings page in the Control Plane interface. It has also been marked as deprecated in the Controller REST API, through which the setting can no longer be modified.
Fixes¶
Cluster document selection is corrected in the case of a new Controller joining a cluster with multiple documents.
Resolved an issue that could cause Controllers to suffer from prolonged shutdowns when restarted.
Client¶
Features¶
bowtie-clion clients gained the commandbowtie-cli wipe-private-keys. This will delete the wireguard private keys on the client.This command should not be used while Bowtie is running.
Arch Linux packages are now available.
Packages for Arch Linux are now available.
Windows: Bowtie should now work correctly when Name Resolution Policy Table (NRPT) rules created via Group Policy are present on the device.
Fixes¶
A bug in the MacOS kernel that sometimes put Bowtie routes onto the default network interface rather than the Bowtie tunnel has been mitigated.
Windows: An occasional delay in processing DNS requests has been addressed.
Windows: more robust communications with Wireguard.
Windows: Properly handle a corrupted Windows private key registry.
Improved tunnel interface management on Windows and MacOS.
MacOS: tunnel exclusions larger than a single host in size are now installed properly into the routing table.
MacOS: Fixed a condition where we incorrectly reported as being in not enforcing.
Linux: Bowtie now works on systems with neither systemd-resolved nor NetworkManager
By default, if neither
systemd-resolvednorNetworkManagerare detected, Bowtie will parse/etc/resolv.confto determine the upstream nameservers. Ifresolv.confchanges, you must restart Bowtie to pick up the changes.The
upstream-resolv-confoption may be used to adjust the location of theresolv.conffile.Another option is to set
upstream-dns-providertostaticand then setupstream-dnsto one or more DNS servers as a comma separated list of IP addresses.
25.12.001¶
Released on 10 December, 2025.
Server¶
Features¶
API keys now report the date and time of their last use.
Change the default rotation method to tolerate slight schema differences. Change to
USE_INTROSPECT_ROTATION=falseto revert to prior method.
Client¶
Features¶
Updated
rpmpackages to provide compatibility across more Enterprise Linux based distributions.
Fixes¶
On Linux, wireguard-tools has been removed as a dependency for bowtie. On RHEL, systemd-resolved is a dependency of wireguard-tools, so this also removes systemd-resolved as a dependency for RHEL.
You may revert to the legacy code path that requires wireguard-tools by using the configuration setting
wireguard-provider="wg-ip"on Linux andwireguard-provider="wireguard-go-plus-wg"on MacOS.
25.11.002¶
Released on 20 November, 2025.
Server¶
Fixes¶
In version
25.11.001many controller metrics were erroneously elided after a dependency upgrade. They have been repaired.
25.11.001¶
Important
This release includes important changes that administrators should review.Released on 13 November, 2025.
Server¶
Features¶
API keys now include attached metadata for the user that originally created the key.
Controller updates may now be managed exclusively from the Control Plane interface along with new options for customization to the update process.
API keys now accept an optional expiration time after which they will no longer be accepted.
Enhancements¶
Updated the base Controller appliance operating system to reflect the latest upstream package updates.
The table below lists relevant user-facing packages that may impact custom configuration settings on deployed Controllers:
Package
Old Version
New Version
Linux kernel
6.1.148
6.1.158
grafana12.0.3
12.0.6
python3.12.11
3.12.12
System services should continue to operate normally across kernel updates, but if you require that the system run on the newer kernel, you should follow-up with any update actions with a system reboot to run on the newer kernel, but this step is not required.
At time of writing, a scan of all operating system dependencies yielded no outstanding critical vulnerabilities requiring immediate action.
Fixes¶
Put additional measures in place to ensure that
loki.servicecan start in situations where the data directory may be misconfigured.
25.10.002¶
Released on 29 October, 2025.
Server¶
Features¶
Reverse proxy configuration state is now included in support bundles.
Added a boot menu entry called
recoverythat permits administrators to login to Controllers in exceptional situations where privileged access may need to be forced (similar in nature to single-user mode).
Fixes¶
Fixed an issue that could cause
restoreoperations on Controllers to fail when reading some configuration values.Added mitigating checks for certain cases in which the reverse proxy configuration for Controllers may be rendered
nullin Caddy.
Client¶
Features¶
Windows:
bowtie.execan now display status and submit SOS’s from the command line.bowtie.exe statusbowtie.exe sos email@example.com note for support(The email address is contact information, it does not have to be an email address. The second parameter is the note submitted with the SOS. Subsequent parameters are added to the note).
MacOS and Linux have been able to use bowtie-ctl in the same way since 25.09.001.
A new configuration variable has been added:
private-dns-forwarder-selection-strategy. This has three possible values:controller-dns(default): Uses the controller mesh for backup DNS handling as well as any routeable servers.direct-routeable: Only uses the directly routeable serversnat64: Uses NAT64 to route directly to IPV4 servers.
controller-dnsis the strategy Bowtie used in versions 2024.08.004 through 2025.09.002.nat64is the strategy Bowtie used in versions 2024.08.003 and earlier.
Fixes¶
Fixed the propagation of DNS Errors. Previously, DNS errors such as
SERVFAILorNXDOMAINwere sometimes propagated asNOERRORwith no results.Default
auto_delete_expired_routestooffas this setting is not appropriate to all conditions.Bowtie’s wireguard interface is now marked in NetworkManager as not managed.
When the client’s
auth-prompt-strategyis set tonever, don’t show a!in the tray icon.
25.10.001¶
Released on 21 October, 2025.
Server¶
Features¶
API keys displayed in the control plane now include metadata about creation and modification timestamps.
The API keys page now offers visibility toggles and copy-to-clipboard.
Controller support bundles now include additional database file timestamp data.
All Controllers now define a consistent, non-zero boot loader timeout to aid with disaster recovery for use cases like entering single-user mode.
The Force Rejoin feature in the Control Plane Sync interface now allows targeting a specific controller for rejoining. When forcing a controller to re-sync to the current document, administrators can optionally select which controller the rejoining controller should sync with, or leave it blank to use any available controller. This can help recover a wider variety of errors.
Controller support bundles may now be collected cluster-wide from the support SoS page.
WAN IP Reporting Feature
Added public IP tracking. This is an optional feature to record device-reported public IP addresses during check-in. Devices now report their WAN IP address to the controller during check-in when enabled. When the public IP changes an audit event is triggered and the device object is changed.
Improved GUI and API for defining
all-v4,all-v6,all-v4-and-v6(Full Tunnel) Site Routes.
25.09.002¶
Released on 28 September, 2025.
Server¶
Enhancements¶
Some adjustments to service resource allocation priorities have been added (for example, changes to
.serviceunitNice=levels andsystemd-oomdsettings). These changes should preferentially keep system-critical daemons alive when under resource constraints.
Features¶
Controller support bundles now include memory diagnostics.
Controller support bundles now include process uptime for
bowtie-server.service.Adds the ability to set next-hop to an interface
Site Ranges can now be targeted at specific users or groups. This can be used, for example, to allow complex IPv4 overlap situations, or conditional full tunnel VPN scenarios.
Fixes¶
Fixed an issue that could cause
soscommands to fail to shell out to diagnostic executables such asperf.Minor fixes to licensing operations to avoid database write amplification. After applying this change, the “last updated” field under the License settings page will reflect the most recent change to a deployment’s license rather than the last time of check-in.
An issue was identified with automatic detection of local networks on boot, occasionally choosing a private network with a self-assigned IP address instead of a more likely RFC1918 address. If
BOWTIE_PRIVATE_IPis not specified, the automatic detection algorithm has been improved.Performance improvement for controller-mediated name resolution.
Began the deprecation of the
/-net/api/v0/organization/controllersendpoint in favor of the/-net/api/v0/organization/controllerendpoint, which is more consistent with the API style. Both endpoints remain active, but we recommend that any requests to the plural/controllersbe changed to the singular/controller.Addressed an issue that could cause high CPU on Controllers with large numbers of devices present.
25.09.001¶
Released on 25 September, 2025.
Meta Control Plane¶
Features¶
Add clarity regarding new Linux packages like
bowtie-gtkandbowtie-coreand when these packages may be preferred.
Client¶
Fixes¶
The DNS server now uses the BIND algorithm when choosing a private upstream DNS forwarder, rather than trying all forwarders in parallel. This algorithm will usually choose the server that was previously the fastest, occasionally choosing a different server to get new measurements.
There are two configuration parameters:
private-upstream-selection-smoothing-constantWhen choosing a DNS server to query for private addresses, Bowtie uses the same algorithm as BIND. It chooses the server with the best smoothed round trip time. This parameter is the smoothing constant for an exponential moving average. The default is 0.7.
private-upstream-selection-decay-constantWhen choosing a DNS server to query for private addresses, Bowtie uses the same algorithm as BIND. Servers that are not chosen have their smoothed round trip time lowered to ensure that they occasionally are retried. This is that decay constant, the default is 0.98.
There are also several Prometheus metrics exported from the algorithm that can be pulled from https://localhost:17134/metrics
The HTTPS status of controllers is now taken into account when choosing a controller for user login.
The user will be sent to one of the controllers that have the “Controller can be used for authenticating users to devices” setting set. (Also known as
can_use_idp). From that set, a controller with a successful HTTPS check-in is chosen.
Features¶
On Linux, bowtie is now available in a package that does not require GUI dependencies.
Bowtie may now be installed via
bowtie-core_amd64-VERSION.debandbowtie-core-VERSION.x86_64-VERSION.rpmpackages. These packages do not contain the tray control application and avoid related dependencies on Linux environments without a desktop environment.Bowtie may be controlled on the command line via bowtie-ctl. Available commands include:
bowtie-ctl enablebowtie-ctl disablebowtie-ctl pausebowtie-ctl resumebowtie-ctl versionbowtie-ctl statusbowtie-ctl sosbowtie-ctl login
bowtie-ctl loginopens a web page in your default web browser.Similarly, the bowtie-gtk tray application is now available in it’s own bowtie-gtk package which may be installed alongside bowtie-core.
Bowtie continues to also be packaged in a package named
bowtie-service_amd64-VERSION.debandbowtie-service-VERSION.x86_64-VERSION.rpmThis is equivalent to installing both bowtie-core and bowtie-gtk. bowtie-core and bowtie-service are marked as conflicts with each other to prevent simultaneous installation.If you wish to switch from bowtie-service to bowtie-core (or vice versa), it is recommended that you either uninstall bowtie-service before installing bowtie-core or that you upgrade bowtie-service to the latest version before installing bowtie-core. Installing bowtie-core over an old version of bowtie-service may not complete successfully.
On Ubuntu and other Debian based distributions, installing bowtie-core via
dpkgwill automatically remove bowtie-service. On CentOS and other Red Hat based distributions, installing bowtie-core viadnfrequires the--allowerasingoption to automatically remove bowtie-service.
Documentation¶
Features¶
Add documentation and download links to the new native iOS app.
25.08.002¶
Important
This release includes important changes that administrators should review.Released on 26 August, 2025.
Server¶
Enhancements¶
The foundational operating system for Controllers has been updated from NixOS 24.11 to 25.05.
This update includes the following noteworthy version changes. If you rely on any of these packages for downstream integrations (such as observability with Grafana and Loki), ensure that the updated versions are compatible with your existing configuration (and update those configurations if necessary).
This change includes an upgrade from Linux kernel version 6.1.135 to 6.1.148. System services should continue to operate normally across kernel updates, but if you require that the system run on the newer kernel, you should follow-up with any update actions with a system reboot to run on the newer kernel, but this step is not required.
Package
Old Version
New Version
Linux kernel
6.1.135
6.1.148
dex2.41.1
2.42.0
grafana11.3.6
12.0.3
loki3.2.1
3.4.4
prometheus2.55.0
3.5.0
python3.12.8
3.12.10
tempo2.6.0
2.7.2
opentelemetry-collector-contrib0.112.0
0.124.0
At time of writing, a scan of all operating system dependencies yielded no outstanding critical vulnerabilities requiring immediate action.
The following updates may require manual intervention on the part of administrators:
jqhas been removed from Controller images due to outstanding and unpatched vulnerabilities. Internal use ofjqhas been replaced with calls to thejaqexecutable (documentation here). If you rely onjqfor custom scripts, consider migrating them tojaq, which is usually a drop-in replacement. For convenience, an alias to thejaqexecutable has been added.opentelemetry-collector-contriboften includes significant changes between minor versions and may require updates to your/etc/otel.yamlfile.
The
promtail.servicelog collection service has been removed in favor of thejournaldopentelemetry-collector-contribreceiver (documentation).promtailis deprecated and no longer receiving updates from Grafana Labs.If you rely on the default observability stack on Controllers to view logs with the default Grafana installation, no action is necessary.
If you consume the log stream in a custom
opentelemetry-collector-contribconfiguration file, then you may want to ensure that exported logs continue to arrive in the expected format. Any custom log exporters defined in/etc/otel.yamlwill still be deeply merged with the default configuration file, which has been updated with a new receiver and processor. The Bowtie documentation has been updated with the latest example of the default receivers and processors.
Features¶
sshdlistener options are now configurable in the Control Plane interface. Administrators may define an organization-wide default or per-Controller settings.opentelemetry-collectorfiles are now configurable from the Control Plane web interface.Support bundles now record CPU use measurements.
Fixes¶
The
bowtie-server.servicedaemon should more reliably report its own version in output logs at startup.
Client¶
Enhancements¶
Network change detection under Linux should be more reliable and incur less ambient CPU load.
Fixes¶
Disabled or deleted devices now correctly recognize their controller side state are able to re-authenticate users from the tray application.
Three related DNS changes in this release.
A change in behavior was enacted to be defensive against consumer ISPs who use DNS interception techniques that overlap with private site ranges.
All requests from the “Help” page to “Evaluate DNS Query” are now logged at
$LOG_PATH/bowtie-dns.logand can be captured by support bundles. This can aid both administrators and Bowtie support in rapid analysis.The wording on that form has changed to be more clear for certain results that match user-supplied rules but are ultimately forwarded upstream.
Fixed an issue that could cause persistent, high background CPU use in some environments.
Linux: eliminated extraneous systemd-resolved restarts.
In prior versions of Bowtie, explicit routing exclusions and DNS routing exclusions were always routed through the default route. This may be incorrect in network scenarios with additional non-Bowtie routing table entries. With this fix, exclusions should now be routed to the correct destination.
Features¶
Collect device posture (e.g. Bitlocker protection status) for Windows.
Extends device posture to Linux
The network name is now displayed in the tray UI when Bowtie believes that the network is available. This network name is the adapter name on MacOS & Windows, and the SSID or a user friendly adapter name on Linux.
This feature may be disabled by setting ui-network-status to false.
Large Bowtie routes (any routes with a network mask of 255.0.0.0 or larger) are now removed from the routing table when a user does not have a connection to the internet (in the absence of a default route). This primarily affects users who are using Bowtie in a full tunnel configuration.
To prevent this behavior, set the device configuration
controller-health-check-strategytoallow-presumptive-connections.
25.08.001¶
Important
This release includes important changes that administrators should review.Released on 1 August, 2025.
Server¶
Features¶
Certificates necessary for Controller SSO configuration files may now be uploaded from the Control Plane web interface.
Custom
prometheusscrape configuration files may now be managed from the Control Plane interface.Improved the “validate hostname” step of the Controller guided setup process to more reliably complete.
Changes to the user-configurable
opentelemetry-collectorconfiguration file (/etc/otel.yaml) now trigger theopentelemetry-collector.serviceto restart.The
otlpreceiver foropentelemetry-collector.servicehas been added to the defaultservices.pipelines.logs.receiverssetting.Optionally send exceptions in the controller to Sentry for analysis. This feature defaults to OFF. If
SENTRY_DSNis set thenbowtie-serverfailures will be automatically emitted to your Sentry install. AdditionallySENTRY_SAMPLE_RATEandSENTRY_TRACES_SAMPLE_RATEcan be set to values between 0 and 10000 (100%) to emit additional metrics. Those also default to 0.When policy metrics tracking is enabled for a Controller, these network policy decision events are now logged. To filter for these events, journal logs for
bowtie-servershould look for output with fields that matchaudit_event=trueandaudit_type=packet_queue.Some default behaviors of
bowtie-server.serviceon Controllers have changed:The
OTLP_GRPC_ENDPOINTis now set to the local OTLP listener by default. This change serves to more tightly integrate the Bowtie daemon with observability tooling.Audit-related events (such as packet flows, user authentication, and more) are now not emitted to standard output (and the system journal) by default. Due to their volume and potentially sensitive nature, they are now only omitted to OTLP endpoints and available over the
logssignal.
Operators currently relying on journal parsing to retrieve audit events should instead refer to the
logspipeline ofopentelemetry-collectorto optionally tap into the stream for other systems. By default, Controllers connect the OTLP log receiver to Loki, so audit events are still available for review but solely within Grafana and Loki rather thanjournald.Network plane activity now records translated NAT64 addresses (if present) when policy decision auditing is enabled.
Network plane activity now records user identifiers, device identifiers, and device hostnames when policy decision auditing is enabled.
A new mechanism has been developed for automatic partition recovery. All controllers will retry all connections without intervention from the user.
Two additional metrics of note are available in
prometheusandopentelemetry:bowtie_server_tcp_sync_manager_peers_we_have_countwith labeltotalshould always match the number of active controllers.bowtie_server_tcp_sync_manager_document_operationswill grow over time, and will aid in observing the database size vs speed of other operations.
Network plane activity now records source and destination ports when policy decision auditing is enabled.
Policy verdict tracking may now be individually controlled between metrics and logs depending on Controller preferences.
Enhancements¶
The default
prometheus.serviceon Controllers now honors the user-controlled directory at/etc/scrape_config_files.d/*.ymlto permit custom scraping endpoints.Third-party telemetry reporting for Grafana Loki has been disabled.
Fixes¶
Fixed an issue that caused
nfqueuemetrics collection to occur when no metrics were present.Ensures that timestamps are correct when emitting logs from the Bowtie server daemon to OTLP endpoints.
Improved the reliability for remote hostname and TLS checks during initial setup, particularly for deployments that only open port
443.Fixed an issue that could cause updates to Bowtie server to fail to take effect when upgrading Controllers.
Handle some edge cases to improve resiliency around provisioning new Controller certificates.
Fixed an issue that could prevent the Bowtie server process from coming online if it failed to find wireguard peers.
25.06.003¶
Released on 26 June, 2025.
Client¶
Fixes¶
Fixed an issue where A records were returned for some AAAA queries when
dns64_strategywas set asnever.Linux: the behavior and appearance of the tray menu should more closely match that of Windows and MacOS.
25.06.002¶
Released on 17 June, 2025.
Server¶
Features¶
Controller host load metrics are now included in support bundles.
Controller support bundles now include limited certificate information as well as sanitized cluster membership information.
A new Grafana dashboard now ships with default Controller installations that visualizes access policy queue metrics.
Marked Controllers images on GCP as
GVNICcompatible.Single sign-on (SSO) files may now be managed via the control plane web interface.
Fixes¶
Fixed an issue with Incus images failing to boot by including EFI-enabled disk images.
In order to prevent a potentially ambiguous boot-up sequence: The configuration file
/etc/bowtie-service.d/document-id.confis specified as the preferred location for theBOWTIE_DOCUMENT_IDparameter.
Meta Control Plane¶
Fixes¶
wgetandcurldownload commands now wrap URLs in quotes to avoid breaking interactions with user shells.
Client¶
Fixes¶
Set the client status to “Initializing” if the block list is not loaded yet. Empty block lists are now handled correctly.
In prior versions, if your authorization timed out you may not be able to access the login page without authorization.
When the external IP address of a Bowtie controller is within the range of a local non-default non-Bowtie network previous versions of the Bowtie client had trouble accessing that controller. This has been fixed.
Connections over https tunnels now work better across network changes.
Linux: fixed a bug in the network status indicator where disabled interfaces were not being properly ignored.
25.06.001¶
Released on 2 June, 2025.
Server¶
Features¶
Controllers now bundle the
ncducommand-line disk usage utility.Controller images now support joining existing deployments with a guided, web-based setup without the need for
cloud-initor manual intervention over the terminal viassh.Single sign-on configuration files may now be uploaded as part of the guided web-based setup steps.
Fixes¶
Fixed an issue that prevented self-signed TLS termination on wildcard HTTP endpoints.
Updated a reverse proxy service daemon setting to ensure that it never enters a permanently-down state.
Client¶
Fixes¶
All current nameservers can be added to our compatibility profile for DoH/DoT for private lookups. To enable this feature, use the new flag
dns-block-doh-dot-current-nameservers = true.Status for DNS enforcing now includes waiting on the DNS block list to download and apply.
Macos: In certain situations 25.05.001 through 25.05.003 preconfigured packages do not install the tray application.
25.05.002¶
Released on 29 May, 2025.
Server¶
Fixes¶
During the initial setup phase, Controllers now flush setup keys to all available
ttydevices.
25.05.001¶
Released on 20 May, 2025.
Server¶
Fixes¶
Fixed a table styling issue on Controller initial setup pages.
A regression preventing the telemetry preferences Control Plane page from rendering sample payloads has been resolved.
Fixed an issue that prevented a system service (
caddy-supervisor.service) from starting correctly.Fixed an issue related to
AllocationUnitsin.ovafiles that prevented them from being imported into certain VMWare environments.Previously, services integral to BGP operation could enter a permanent-down state. New configuration changes ensure that attempts to restart an unhealthy BGP daemon will never fail permanently, but persistently retry with a moderate backoff.
Note: BGP services may be inoperative but fail to broadcast network unavailability to other cluster peers, causing incorrect or unreachable routes. Investigative work into this failure mode is ongoing, but this change should mitigate some cases.
Fixed an issue that could cause reverse proxy configuration changes to fail on Controller update.
Configuration files for Controller DNS are now included in Controller support bundles.
Fixed an issue that could unintentionally cause
systemd-networkdto restart on system update, potentially resulting in impacts to network connectivity.Previously client configuration specific to user groups could be applied to accepted devices which were not yet associated to users. This has been resolved.
In 25.03.003 an issue was observed where the DNS server on controllers could bind to an incorrect address. This is now checked and resolved at
bowtie-serviceboot.Cross Site DNS regressed in 25.03.003 clients with 25.03.003 controllers for some installations. A fix for these environments has been applied at the controller.
During database maintenance, a defect where device groups may be lost between versions 2025.01.001 and 2025.03.003 has been resolved.
Enhancements¶
Updated the base Controller appliance operating system to reflect the latest upstream package updates.
The table below lists relevant user-facing packages that may impact custom configuration settings on deployed Controllers:
Package
Old Version
New Version
grafana11.3.4
11.3.6
linux6.1.130
6.1.135
nix2.24.12
2.24.14
caddy2.9.1
2.10.0
Vulnerabilities closed due to updated packages or backported patches include:
Vulnerability
Package
Mitigation
CVE-2024-56406
perlPatch backported by upstream
At the time of writing, a scan of all operating system dependencies yielded no outstanding critical vulnerabilities requiring immediate action.
When upgrading your Controller, please bear the following release notes in mind:
This update includes an update from Linux kernel version 6.1.130 to 6.1.135. System services should continue to operate normally across kernel updates, but if you require that the system run on the newer kernel, you should follow-up with any update actions with a system reboot to run on the newer kernel, but this step is not required.
Features¶
Controller images are now available for Incus and LXD.
Controllers now support the ability to create time-limited, serial console-only administrative user accounts for shell access from the Control Plane web interface. This feature is intended to aid administrators who may require host-level access without predefined access configured, such as via
ssh. Consult the user documentation for temporary console users for additional information.Note: the addition of this feature does not create temporary administrative users by default, and may be disabled organization-wide if desired. Additionally, access is constrained to the equivalent of physical access to the controller. This feature does not enable remote access.
Client¶
Fixes¶
Fix the entrypoint dialog so clicking “Connect” works, in addition to pressing Enter on the text field.
Fix a hang when setting the entrypoint in the configure dialog after a fresh install.
Log errors gracefully when setting the tray icon.
Flush the system-wide DNS cache after the DNS block list changes
MacOS: A bug in Bowtie versions 25.02.001 through 25.03.003 has been fixed. Bowtie networks stopped working when the default route moves to another interface, such as when switching between Wi-Fi and Ethernet.
In previous versions, the DNS filters may not have been available at client start. This has been corrected.
A compatibility mode has been added to allow docker containers in Linux to access private DNS.
Windows: A bug was found and fixed in the system that monitors the health of the Bowtie DNS system. This bug was introduced in 24.11.001 and fixed in 24.05.001.
Features¶
Private nameserver lookups have improved performance. Additionally, there is a new DNS flag to shape behavior for upstream name servers. Lower timeouts can improve user experience for many cases so the default has been lowered. Additional changes to defaults may come as we collect more data in our environments.
private-upstream-timeout-ms: This was previously set at 5s and was not configurable. It has been reduced to 1.75s for the default.
DNS audit logging now works on both Linux and Windows.
This adds the setting
dns_audit_log_directory. On Windows this defaults to a path underC:\ProgramData\Bowtie\log, on Linux this defaults to a path under/var/log/bowtie. This setting is only read at startup, it does not reload at runtime.A new setting is introduced for auditing client DNS events. Device config key
dns-audit-levelcan be set to values “errors-only”, “blocked-queries”, “all-queries”, or “all-queries-all-answers” to log DNS queries and answers to a specified location on clients. The logs are written as JSONL following Elastic Common Schema.dns-audit-levelis dynamic, it reloads on each DNS request.log-directoryis not dynamic and takes effect only on client startup.Enable DNS audit logging on macOS.
Support bundle packages now record the date and time they were collected.
The configuration flag
ui-network-statusis added to control the network status line in the tray application, and is enabled by default.There is a new line in the tray menu reflecting network status. If this status line reports failure, it means the Internet access is unavailable.
Documentation¶
Fixes¶
Support for deploying Controllers on Kubernetes is undergoing frequent changes. Some sections of the documentation have been updated to reflect this.
If your organization requires the ability to deploy on Kubernetes, please reach out to a member of our team, who will be able to assist.
25.03.003¶
Released on 31 March, 2025.
Server¶
Enhancements¶
Introduced additional safeguards around Controller REST endpoints. This is a preemptive defense in depth measure; control plane functionality should remain unaffected.
Features¶
First-run installations for Controllers that undergo the
/setupprocess now support loading pre-existing (bring-your-own) TLS certificates.
Fixes¶
Fixed an issue that could cause reverse proxy configuration updates to fail to apply correctly.
The
soscommand now asserts that the user has sufficient privileges to work correctly.Added additional measures to prompt retries when acquiring TLS certificates from ACME providers when failures occur.
Client¶
Fixes¶
In prior versions, locally scoped IPv6 upstream DNS servers were ignored. This has been resolved and clients having issues on networks that are primarily using DNS64 or other locally-scoped DNS servers have been repaired.
Private DNS lookup now forward to the controller’s DNS server rather than directly accessing the upstream private DNS server. This reduces resource consumption.
Fix stderr redirection (only affects Windows) when the stderr file is deleted.
The strategy for network interface configuration changes on Windows for the private Bowtie interface caused state tracking issues when connecting to many controllers at the same time, such as immediately after pause/resume cycles. The strategy has been adjusted to correct for this condition.
Features¶
WireGuard logs are split off into files with
_wgto make the main logs easier to read.Adds optional Sentry integration for error reporting. If the
sentry-dsnis set, errors will be reported to Sentry. This allows for better monitoring and debugging of issues in production environments. It can further be controlled bysentry-sample-rateandsentry-traces-sample-rate. These are sent as integer values from 0 to 10000. They default to 100% (10000) for error samples and 10% (1000) for trace samples.
25.03.002¶
Released on 18 March, 2025.
Server¶
Enhancements¶
Updated the base Controller appliance operating system to reflect the latest upstream package updates.
The table below lists relevant user-facing packages that may impact custom configuration settings on deployed Controllers:
Package
Old Version
New Version
grafana11.3.2
11.3.4
linux6.1.123
6.1.130
python3.12.7
3.12.8
git2.47.0
2.47.2
Vulnerabilities closed due to updated packages or backported patches include:
Vulnerability
Package
Mitigation
CVE-2024-52006
gitUpdated to patched version
CVE-2024-52005
gitUpdated to patched version
CVE-2024-50349
gitUpdated to patched version
CVE-2024-56171
libxml2Updated to patched version
CVE-2025-24928
libxml2Updated to patched version
CVE-2024-12797
opensslUpdated to patched version
CVE-2024-9143
opensslUpdated to patched version
CVE-2024-13176
opensslUpdated to patched version
At the time of writing, a scan of all operating system dependencies yielded no outstanding critical vulnerabilities requiring immediate action.
When upgrading your Controller, please bear the following release notes in mind:
This update includes an update from Linux kernel version 6.1.123 to 6.1.130. System services should continue to operate normally across kernel updates, but if you require that the system run on the newer kernel, you should follow-up with any update actions with a system reboot to run on the newer kernel, but this step is not required.
Fixes¶
Added service manager settings that retry failed attempts at running
dex.service.Fixed an issue when collecting BGP related logs from Controller SoS bundles.
Added service manager settings that retry failed attempts at running
hostname-setup.service.Fixed an incorrect
systemdsetting for the backup daemon.Updated the Controller command-line based support bundle utility to resolve deprecation warnings.
A feature introduced in 25.03.001 to reset partial connections was shown to be unstable in some environments and is being disabled for further evaluation. Set
WIREGUARD_ENABLE_KERNEL_LOGGING=trueto enable.
Features¶
The bandwidth consumption of the Control Plane interface has been greatly reduced, now measuring roughly 1% of previous usage.
The initial Controller setup page is now gated behind authentication. See the setup documentation for additional information.
25.03.001¶
Released on 18 March, 2025.
Meta Control Plane¶
Fixes¶
Updated the list of Windows and macOS versions to reflect more accurate client support coverage.
Client¶
Features¶
Toast notifications on Windows are now clickable.
The default
tunnel_rebuild_strategyis nowRebuildOnAllUnreachable. This will reset the connection on certain connectivity issues.Bowtie may now be configured to ask users for a reason when they pause. The user’s responses are collected and periodically uploaded to the controller, where they can be viewed by the Bowtie administrator.
A new client configuration option has been added,
allow-route-conflict-override.Bowtie does not install IP routes that shadow existing system routes. For example, if you have set up a Bowtie Site with a range of 192.168.5.0/24 but the user’s device already has a route of 192.168.4.0/22, Bowtie will not install the 192.168.5.0/24 route because that may break the user’s local network. Previously, the only way that users with this conflict could access the 192.168.5.0/24 site network was by using NAT64 translation.
This new option allows this behavior to be overridden. In the above example, you can add 192.168.4.0/22 to
allow-route-conflict-overrideto allow installation of the 192.168.5.0/24 route.This default value of this option is “10.0.0.0/8”. To return to previous behavior, set this client configuration option to an empty string.
The format of this is a comma separated list of IP address ranges.
Fixes¶
Allow the DNS service to run as a single process.
25.03.001 changes the service management approach on windows.
This will improve reliability at the point of upgrades by using native windows service control management and reduce an erroneous dialog in the MSI subsystem.
Close the tray application after
StopServicesin the MSI.If we close the tray application while the main service is still running, the main service’s UI supervisor feature may restart the tray application, causing the installer to see
bowtie.exeas locked and prompt for a system reboot.Closing the tray application after the service is stopped should ensure that it stays closed during the update.
In Windows, reading interface statistics on certain interfaces has occasional failures. Earlier versions of Bowtie reset the interface on a single read error. Bowtie now defaults to 3 consecutive read errors and this can be tuned with the
interface-error-reset-countflag.Windows: logs are now limited to 50MB per file, with a maximum of 5 files per service.
Obey the shutdown signal in the
block listtask of the main service.This improves graceful shutdown behavior but does not totally fix it, sometimes there is still a timeout.
Bowtie will now reopen the login tab if a session expires or is forcibly disassociated.
Fixes the “The setup was unable to automatically close all requested applications.” dialog box on Windows.
Add an option to run the service as a Windows service directly, instead of using the
winswwrapper.See the changelog in
crates/bowtie_servicefor details.
Deprecations¶
Previously Verisign and Hurricane Electric public DNS servers were configured as fallback options for both IPv4 and IPv6 to prevent certain local failure modes. Now
dns_fallback_ipv6will default to empty values, to prevent issues in split-horizon DNS environments.
25.02.001¶
Important
This release includes important changes that administrators should review.Released on 8 February, 2025.
Server¶
Enhancements¶
Additional logging from
systemdis now included in Controller support bundles.The foundational operating system for Controllers has been updated from NixOS 24.05 to 24.11.
This update includes the following noteworthy version changes. If you rely on any of these packages for downstream integrations (such as observability with Grafana and Loki), ensure that the updated versions are compatible with your existing configuration (and update those configurations if necessary).
This change includes an upgrade from Linux kernel version 6.1.119 to 6.1.123. System services should continue to operate normally across kernel updates, but if you require that the system run on the newer kernel, you should follow-up with any update actions with a system reboot to run on the newer kernel, but this step is not required.
Package
Old Version
New Version
Linux kernel
6.1.119
6.1.123
cloud-init24.1
24.2
grafana10.4.13
11.3.2
loki3.1.2
3.2.1
opentelemetry-collector-contrib0.101.0
0.112.0
prometheus2.54.1
2.55.0
promtail3.1.2
3.2.1
python3.11.10
3.12.7
tempo2.4.2
2.6.0
Controllers now ship with a more comprehensive set of
terminfofiles to facilitate better client remote connection support.Controller updates now offer more fine-grained information regarding whether an update procedure either succeeds or experiences unexpected behavior.
Fixes¶
Controller observability tooling was previously instrumenting all URLs, whether valid or not. Changes to the default Prometheus configuration now proactively drop URLs for paths with
404responses to reduce noise and improve performance along withaxum_http_requests_pending.
Features¶
It has been observed that network partitions over a certain length (roughly 20 minutes) are not automatically recoverable and require a restart of some control plane components. To recover automatically in these scenarios via automatic server restart on peer failure, enable the “Minimum Peers Behavior” setting in a Controller’s settings in the Control Plane interface. By default, the setting is disabled to retain existing behavior and prevent spurious restarts.
The “Minimum sync peers” field controls how many other Controllers the Controller being configured must be connected to before it is considered unhealthy. If using the setting, the number should be less than your cluster size, but greater than the number of Controllers at your site. This number is likely between 1 and 3 for most installations, and has a minimum value of 1.
The “Sync-unhealthy duration” field controls how long (in seconds) it takes for the Controller being configured to restart after its number of connected peers falls below the set minimum. The minimum value of this field is 120 seconds.
This setting can also be updated using the Controller REST API, with the
/-net/api/v0/organization/controllerPOST endpoint.Note that updating the Minimum Peers Behavior setting for a given Controller will restart it.
Further work is ongoing to make automatic recovery less disruptive and require less up-front consideration.
Meta Control Plane¶
Features¶
The staging meta control plane (available for software downloads like release candidates) now has a more user-friendly URL at https://dev.api.bowtie.works available for general use.
Client¶
Features¶
Adds
dns-capture-exclude-cidrsflag to allow bypassingbowtie-dnsfor one or more address ranges. This expandsdns-capture-and-forwardstrategies to allow additional options for some software to pass bowtie unobstructed. CIDRs are delimited by a comma. Example:dns-capture-exclude-cidrs = "10.193.0.0/16,10.194.0.0/16"MacOS clients have now packaged wireguard-go as the default tunnel provider. Set
wireguard-provider="Boringtun"to go back to prior functionality.
Fixes¶
Improved behavior when installing or uninstalling Windows packages that should avoid notifications about needing to restart or failing to close the Bowtie client.
25.01.001¶
Released on 9 January, 2025.
Client¶
Fixes¶
Exit the tray app process cleanly when the main loop task ends.
Previously on Windows, installing a new MSI would try to close the UI, but the UI would hang instead of exiting its process.
24.12.001¶
Released on 20 December, 2024.
Server¶
Enhancements¶
Updated the base Controller appliance operating system to reflect the latest upstream package updates.
The table below lists relevant user-facing packages that may impact custom configuration settings on deployed Controllers:
Package
Old Version
New Version
grafana10.4.8
10.4.13
linux6.1.111
6.1.119
loki3.1.1
3.1.2
python3.11.9
3.11.10
Vulnerabilities closed due to updated packages or backported patches include:
Vulnerability
Package
Mitigation
CVE-2024-48958
libarchiveUpdated to patched version
CVE-2024-48957
libarchiveUpdated to patched version
CVE-2024-8006
libpcapUpdated to patched version
CVE-2023-7256
libpcapUpdated to patched version
At the time of writing, a scan of all operating system dependencies yielded no outstanding critical vulnerabilities requiring immediate action.
When upgrading your Controller, please bear the following release notes in mind:
This update includes an update from Linux kernel version 6.1.111 to 6.1.117. System services should continue to operate normally across kernel updates, but if you require that the system run on the newer kernel, you should follow-up with any update actions with a system reboot to run on the newer kernel, but this step is not required.
Additional system messages are included in Controller support bundles.
Features¶
User auditing events that occur over Bowtie tunnels now include additional address metadata about the public network address served by the tunneled interface.
Controllers now scale the
nf_conntracksysctlsetting for optimal values. Previously, Controllers serving large volumes of traffic could exhibit session exhaustion resulting indropped packetmessages in some cases.
Fixes¶
Network Interface reconciliation of routing tables and
iptablesrules previously only listened to changes coming from configuration. Now reconciliation events are considered from any change tonetlink’s routing table, link state, or IP address assignments as well. Additionally reconciliation is clamped to also be evaluated periodically as a fallback.
Meta Control Plane¶
Fixes¶
Updated client package macOS compatibility to reflect that versions 14 and 15 are supported.
Client¶
Features¶
A new experimental routing provider for Windows that should substantially reduce energy consumption has been added. To enable, set the
routing-providertonet-io-api. This will likely become the default in future releases.There is a new tunnel health checking mechanism. It uses a configurable
persistent-keepaliveon the tunnel interface to actively send zero-data length packets if the connection is quiet and bandwidth telemetry to passively determine tunnel health. The keepalive timer should match on the client and the controller. Enabling this feature requires environment variable configuration on every controller and client configuration on every client that you want to opt-in to tunnel rebuilds.This feature requires active data sent from the client and the controller. Persistent keepalives send a signed zero-length packet at a minimum interval on an otherwise quiet connection. You should set the persistent keepalives to the same value on clients and controllers.
Set persistent keepalives on your controllers with this environment variable
BOWTIE_WIREGUARD_PERSISTENT_KEEPALIVE=25Set persistent keepalives, and tunnel health failure boundaries on clients with these parameters:
persistent-keepalive=25 unhealthy-tunnel-health-count=10 tunnel_rebuild_strategy=RebuildOnAllUnreachable
This says “If telemetry counts are invalid for 25 * 10 seconds, then rebuild tunnels”
Effectively, this will:
Rebuild tunnels on wake-from-sleep
Rebuild tunnels on implementation issues and severe network partitions
It is our expectation that this feature will become stable and default soon when bandwidth and CPU costs of it’s operation decrease.
There are two levels of enforcement. We currently recommend first trying
tunnel_rebuild_strategy=RebuildOnAllUnreachableto opt into tunnel rebuild on failure.Device to Controller Check-ins and Tunnel Statistics are now recorded to the local data store. Approximately 24h of active check-in responses are stored, and approximately 2 days of tunnel statistics are stored. Configuration defaults are:
store_maximum_checkin_response_rows=1440. This is approximately 24 hours of 1 minute check-insstore_maximum_tunnel_stats_rows=1728000. This is approximately 2 days of 1 second stats for 10 controllers
On Windows, DNS policy enforcement now uses a more energy efficient interface
On Windows, a new DNS supervisor strategy is implemented to improve performance and reduce energy use.
Documentation¶
Enhancements¶
Prevented support requests from being submitted twice at the same time and clean up the support tickets fields’ once submitted.
24.11.002¶
Released on 14 November, 2024.
Server¶
Features¶
NAT64 data flows multiplex over limited port resources on each controller. 24.11.002 tunes the size of the pool, as well as reduces the number of data flows that require NAT64.
Fixes¶
24.11.001 introduced TCP support in the client DNS requests. 24.11.002 ensures that in all circumstances this traffic can transit the access policy engine.
24.11.001¶
Released on 12 November, 2024.
Server¶
Fixes¶
Fixed an issue that prevented Controllers from correctly provisioning locally self-signed certificates for local IP addresses.
Increased the grace period that Controllers will allow when updating their BGP routes. Intermittent network latency fluctuations should result in reduced BGP configuration flapping.
Features¶
If your public IPs are static, and if you always have public IP access to your controllers (via public access or hairpin NAT) a new Wireguard Hint field has been added to the cluster configuration. This will allow the clients to use the “Hint” IP for the Wireguard connection, instead of the DNS name. If you are connecting to your Bowtie controllers from the same network as your Bowtie clients, care must be taken to ensure that hairpin NAT is configured if they are using private IP addresses. If you are relying on split horizon DNS this implementation is not yet applicable to your environment.
Client¶
Features¶
SOS submissions may now be retried in case of errors to publish.
Several improvements have been made to private name resolution. If multiple DNS servers are eligible, records will be requested in parallel, preferring the fastest result. EDNS and DNS over TCP are now enabled for private names, allowing very large records to be returned.
Important pre-release quality feature.
controller-health-check-strategy. In previous Bowtie client versions, networks equal or greater to “/8” (e.g 10.0.0.0/8 or 0.0.0.0/1 for full tunnel) would not be installed until several health checks had passed. This is to prevent users from having “no internet” scenarios in captive portal situations. This flag can now be set toallow-presumptive-connectionswhich will install the routes while Bowtie is Active, before health checks have passed. The next two versions will continue to improve on this strategy. If this flag causes issues, revert it torequire-health-checkto restore 24.10.003 default behavior. To manually bypass a captive portal while this flag is on, pause your Bowtie client. If this feature is right for your environment, consider client configuration targeting to deploy to a subset of your users.Improved Active Directory integration for remote connections
Fixes¶
Improvements in window handling in macos.
Improvements for private name handling in IPv6-only networks when managed domains are in overlay mode.
DNS health checks have also received several improvements. First, all health checks are now forced over the local upstream connection rather than allowed through the tunnel, which ensures a clear read of the client’s network environment. Second, the health check system is now respecting the probe’s TTL, which creates more accurate checks in full-tunnel scenarios and reduces noise on the network.
Fixed an issue in the Windows DNS supervisor causing errant service restarts when upstream connectivity is inconsistent.
Improved route handling for service and machine stop/start and wake/sleep events.
Improved route handling for machines with multiple active network interfaces
Documentation¶
Enhancements¶
Clarified the scope of the Control Plane devices permission as it applies to user information.
24.10.003¶
Released on 29 October, 2024.
Server¶
Features¶
Log out and log in buttons are now more prominently displayed on Control Plane pages.
The
conntrackutility is now available on Controllers by default.If a Controller SoS fails to send correctly, the bundle payload is now cached for a short period of time. Administrators may optionally choose to retrieve this file to share out-of-band in situations like air-gapped Controllers or when the submission API endpoint is otherwise unavailable.
Controller support bundles now include more-complete wireguard interface information. Private keys are not included.
The Control Plane settings interface now enforces correct values for web filtering collections if present.
Fixes¶
Fixed broken links to collections when configuring web filtering.
Closed an avenue for server information disclosure in the
sos.servicedaemon.Grafana’s cookie security defaults have been hardened.
Resolved an issue with BGP functionality that negatively impacted service availability on reload.
Fixed an authentication route that could potentially expose an open redirect.
Patched a bug in Controller clustering that would cause excessive traffic and log noise about peer members being known as new, different peers.
Controllers now enforce stricter
Set-Cookiesettings.
Client¶
Features¶
When generating support bundles, users can now optionally add support details and contact information to their submission.
Fixes¶
Updated the help menu item so it focuses the help window if it already exists.
Previously server-sent configuration would not apply until after the first successful API command after boot. Now stored server-applied configuration is loaded at boot time.
24.10.002¶
Released on 10 October, 2024.
Client¶
Features¶
In
prefer-tunnelAPI mode we now return both IPv4 and IPv6 addresses for browser requests. This improves the user login experience when switching networks between on-site and Bowtie networks.
Fixes¶
Fixes a regression in windows search domains.
24.10.001¶
Released on 9 October, 2024.
Server¶
Features¶
Controller
gceandgce-efiimages now includegoogle-cloud-sdk.Logs related to supporting BGP daemons are now included in Controller support bundles.
A grace period can be configured for user authentication sessions. on the /configuration page if you have user device disassociation time set you may also set a grace period. For example if you set the timer to 12 hours, and the grace period to 1 hour, the user will be prompted starting at hour 11 after authentication, but the policy engine will not disassociate the user and the device until hour 12.
Logging verbosity around device<->user binding and user authorization has increased. All events regarding this are labeled
audit_event=trueAccess policy performance for TCP flows has increased.
Fixes¶
Fixed an issue in which
mgmtd-config.serviceorbgpd-config.serviceunits might have failed during Controller upgrade.The
/sosHTTP endpoint now denies access unless the request originates from a logged-in user. If you need public access for Controller SoS bundles, consider using the Control Plane support page, the port:911HTTP endpoint, or thesosterminal command.Controllers would sometimes run the
zebra.servicedaemon even when BGP was not enabled. This service now only runs when necessary.In 24.09.007 gossiped ephemeral messages between nodes in large clusters could pass a size boundary which would crash the node. These messages are now dropped and logged.
Meta Control Plane¶
Features¶
A new field named
commentaryis now present on reported vulnerabilities. If set, the contents of the field explain why the vulnerability presents a reduced risk to the given software package.
Client¶
Features¶
Previously the re-authentication mechanism may prompt before it was possible (by network circumstance) to authenticate. This build checks for an “OK” response from the required endpoint before prompting the user.
Fixes¶
In 24.09.007 an issue where the highest upgrade would be re-applied has been resolved.
24.09.007¶
Released on 27 September, 2024.
Server¶
Enhancements¶
Updated the base Controller appliance operating system to reflect the latest upstream package updates.
The table below lists relevant user-facing packages that may impact custom configuration settings on deployed Controllers:
Package
Old Version
New Version
bash5.2p26
5.2p32
grafana10.4.6
10.4.8
linux6.1.104
6.1.111
prometheus2.53.1
2.54.1
Vulnerabilities closed due to updated packages or backported patches include:
Vulnerability
Package
Mitigation
CVE-2024-41815
starshipBackported patch
CVE-2023-42366
busyboxBackported patch
CVE-2023-42365
busyboxBackported patch
CVE-2023-42364
busyboxBackported patch
CVE-2023-42363
busyboxBackported patch
At the time of writing, a scan of all operating system dependencies yielded no outstanding critical vulnerabilities requiring immediate action.
When upgrading your Controller, please bear the following release notes in mind:
This update includes an update from Linux kernel version 6.1.104 to 6.1.111. System services should continue to operate normally across kernel updates, but if you require that the system run on the newer kernel, you should follow-up with any update actions with a system reboot to run on the newer kernel, but this step is not required.
Features¶
Controller support bundles now accept an optional contact and problem description field.
Controllers now make
pythonavailable in-$PATHfor use with tools that require an interpreter likeansible. At time of writing, the bundled python version is 3.11.9.Controllers now emit all user authentication events in their server logs. When viewing
bowtie-server.servicelogs on the Controller directly, via Grafana, or aggregated throughopentelemetry-collector, these auditing log events are annotated withaudit_event=true. You may use this field to narrow searches for user authentication activity in the log event stream.The types of auditing events include successful authentication, denied authentication (through invalid credentials or disabled users), and initial authentication flow requests. Wherever possible, these events include source IP metadata derived from the best possible source (deferring to IP forward headers and falling back to direct peer network address).
Add the ability to specify next_hop for any site’s range.
Fixes¶
Set a
cloud-initoption that should avoid losing manual address assignments on network interfaces via DHCP.Enabled the Controller
mgmtddaemon to facilitate multi-hop routing when required.
Meta Control Plane¶
Features¶
Vulnerability reports for each Controller artifact are now reported alongside other download metadata. Consult the vulnerability API documentation for additional information.
Scans are performed on a regular basis for current Controller versions.
Client¶
Features¶
To provide enhanced device security, Bowtie has begun storing device-specific secrets in the operating system’s secret storage mechanism instead of privileged files on the operating system. Retrieval and use of those secrets is currently locked behind a feature flag. Set
--state-strategy=LoadFromStateDbto prefer the SQLite DB and OS Secret storage mechanism. Future releases will remove existing privileged files and default to OS Secret storage.API communications over the Bowtie tunnel are now supported. Previously both TCP443, for API communications and a UDP port for tunnel communications were required. Bowtie will now allow TCP connections over the tunneled connection. This will allow in many scenarios a greatly reduced public surface area of your secure infrastructure. This mode of operations currently requires bootstrapping each device with accessible HTTPS connections either via a privileged connection (like in-office) or temporary access over the tunnel (like allowing a specific device through your firewall for TCP443 for a temporary amount of time). Future iterations may allow easier device bootstrapping through alternate channels. If you are interested in other modes of operation please discuss it with your Bowtie representative. To enable this functionality set
controller-api-strategy=prefer-tunnel.The
software-update-strategyconfiguration variable gained a new value:auto-managed-in-range(min_version, max_version)With this strategy, updates are managed by Bowtie, but only within a specific version range (inclusive). If the current version is within the range, no updates are performed. If the current version is outside the range, an update will be performed to the highest available value within the range. Example configuration file entry:
software-update-strategy = "auto-managed-in-range(24.09.006, 24.09.008)".There are 4 new auto-update configuration variables:
software-update-time-start: The start of the time window within which auto-updates are allowed to be installed. If
software-update-time-startis greater thansoftware-update-time-end, the window includes midnight. Ifsoftware-update-time-startis equal tosoftware-update-time-end, the window is all 24 hours. Default: midnight. Time format: “HH:MM:SS”, where HH is 00-23. Times are specified in local time.software-update-time-end: The end of the time window within which auto-updates are allowed to be installed. If
software-update-time-startis greater thansoftware-update-time-end, the window includes midnight. Ifsoftware-update-time-startis equal tosoftware-update-time-end, the window is all 24 hours. Default: midnight. Time format: “HH:MM:SS”, where HH is 00-23. Times are specified in local time.software-update-interval: How long to wait between auto-update checks. May be specified like “10d”, “10h”, “10s”. Quotes are necessary in TOML configuration files. Default: “1d”.
software-update-delay: How long to wait after starting Bowtie before the first auto-update check. May be specified like “10d”, “10h”, “10s”. Quotes are necessary in TOML configuration files. Default: “1h”.
Fixes¶
Windows & Linux: downloaded auto-update packages are deleted immediately after use rather than relying on the operating system’s temporary directory cleanup mechanism.
24.09.006¶
Released on 17 September, 2024.
There are no release notes for this version.
24.09.005¶
Released on 13 September, 2024.
Server¶
Features¶
Controllers now print their network interface information to the serial console at boot time to aid with operational diagnostics.
Fixes¶
Fixed an issue that would cause the
backupdbackup daemon to try and fail to start indefinitely on pre-bootstrapped Controllers.For LDAP Sync Jobs: A defect in our pagination approach was preventing any results from being returned for large queries of Groups. The output of the LDAP sync task has been truncated to report statistics and sample the first result for additions.
Client¶
Features¶
A new configuration option for MacOS can aid in co-existence with other networking software that uses
pf. If you have custom anchors in pf you can addanchor-excludes=someanchor,otheranchorand the Bowtie client will ignore those rules when adding its own.
Fixes¶
Bowtie works hard to play nicely with other networking software on your computer. Our persistence mechanism on MacOS for making sure other software plays well with us has proven to be stable and effective in a large variety of circumstances. The heartbeat mechanism for this check has been reduced from 2 minutes to 30 seconds.
A routing calculation defect was introduced and identified in MacOS on 24.09.004.
24.09.004¶
Released on 10 September, 2024.
Server¶
Fixes¶
Fixed some cases in which updates would cause the Control Plane UI to fail to load.
We have resolved an issue where incomplete configurations of BGP mode could leave a controller in a crash loop.
Features¶
The IPv4 Pools page has changed to make selecting routing strategy decisions easier to understand, and explicitly listing every available option.
24.09.003¶
Released on 5 September, 2024.
Client¶
Fixes¶
In 24.09.002 on MacOS Bowtie DNS would not be functional concurrently with the Operating System’s “Internet Sharing” feature. This is resolved in 24.09.003
24.09.002¶
Released on 5 September, 2024.
Server¶
Enhancements¶
Updated the base Controller appliance operating system to reflect the latest upstream package updates.
The table below lists relevant user-facing packages that may impact custom configuration settings on deployed Controllers:
Package
Old Version
New Version
grafana10.4.4
10.4.6
grafana-loki3.0.0
3.1.1
linux6.1.96
6.1.104
prometheus2.52.0
2.53.1
promtail3.0.0
3.1.1
When upgrading your Controller, please bear the following release notes in mind:
This update includes an update from Linux kernel version 6.1.96 to 6.1.104. System services should continue to operate normally across kernel updates, but if you require that the system run on the newer kernel, you should follow-up with any update actions with a system reboot to run on the newer kernel, but this step is not required.
At the time of writing, a scan of all operating system dependencies yielded no outstanding critical vulnerabilities requiring immediate action.
Fixes¶
The
qemuguest agent now runs on allqcowandqcow-efiformats (conditionally upon whether the host is running inside ofqemu).The Controller Control Plane web interface now has more targeted caching headers set to ensure that the correct assets are used. This bug would manifest as web interface bugs following a Controller version update.
Addressed an issue that could cause Control Plane web pages to present
Content-Security-Policyloading errors resulting in an empty white screen.Improved
Content-Security-Policyhandling by proactively caching assets.
Features¶
Up to this point, Bowtie has only allowed routing via NAT through our controllers. Significant changes have been made to allow preview release of highly-available direct routing via BGP participation at your sites.
With this change, a previously required kernel module is not necessary in all circumstances.
--enable_nat64_kernel_module=falsecan now be used on controllers where no NAT64 capability is necessary.Controllers now have the ability to selectively block IP addresses or CIDR networks from control plane web access. Reference the web filter documentation for additional information.
Client¶
Features¶
A mechanism to limit CPU usage was added.
This also should help limit runaway logs.
Fixes¶
In Version 24.09.001 a regression occurred in allowing private names to be resolved with some DNS configurations.
24.08.003¶
Released on 9 August, 2024.
Server¶
Features¶
Controllers now support in-browser chat-based support options for licensed customers. Refer to the support chat documentation for additional information about this feature.
Device limit counts are able to be set per user and globally. Users will be redirected to
/device-auth-limit-reachedif they log in to a device which exceeds their authorization level.New features have been added to the Configuration section to remove or disassociate stale devices which have not checked in over some time (greater than one week). If those options are set then devices will be scanned hourly.
Additionally broadcast, and cache device check-in data between all controllers so that more accurate “last seen” information can be found in the API.
Client¶
Features¶
Added support for Ubuntu 20.04.
“kebab-case” is now allowed in client configuration files.
Prior to this update, configuration files contained lines like
dns_capture_and_forward_strategy = "AllowAlternatePrivateF1"
Now, “kebab-case” is allowed for both key and value:
dns-capture-and-forward-strategy = "allow-alternate-private-f1"
The old casing is still accepted but the documentation will recommend “kebab-case”, primarily due to its similarity to the usage of the same parameter on the on command line:
$ bowtie-service --dns-capture-and-forward-strategy=allow-alternate-private-f1 service
Fixes¶
IPV6 fix for
dns_capture_and_forward_strategy = "AllowAlternatePrivateZ1AndS1"
24.08.002¶
Released on 2 August, 2024.
Client¶
Fixes¶
Version 24.08.001 was released with an executable component on windows that was not signed by our CI. This package has been pulled and this is resolved in 24.08.002
24.08.001¶
Released on 2 August, 2024.
Server¶
Fixes¶
Version 24.07.005 included a change to open the Controller’s reverse proxy to respond to any inbound request with TLS (regardless of hostname). This change has been made more consistent to also respond with a self-signed certificate (if necessary) to requests from any IP address as well.
Client¶
Features¶
In order to mitigate caching concerns, upstream health checks have migrated to a payload-based approach.
MacOS: a new strategy was added to allow coexistence with an alternate VPN solution.
Enable with
dns_capture_and_forward_strategy = "AllowAlternatePrivateZ1AndS1"in your configuration file.
24.07.007¶
Released on 26 July, 2024.
Client¶
Features¶
Windows:
NrptRuleshas been made the default DNS injection strategy. To restore the previous behavior, add to your configuration file inC:\ProgramData\Bowtie\configuration\the linelocal_dns_provider = "RegistryInjector".Three new options have been added to the DNS supervisor to modify the behavior of the DNS supervisor on Windows.
// These are the defaults dns_healthcheck_failure_uninstall_count: 3, dns_healthcheck_local_timeout: 150, # Milliseconds dns_healthcheck_upstream_timeout: 500, # Milliseconds
The previous default for
dns_healthcheck_failure_uninstallcount was 1. In low-quality internet scenarios increasing this counter may help keep connections stable. The other behaviors have not changed by default.
Fixes¶
Red Hat / CentOS Linux: fixed errors in the uninstall and upgrade scripts for 24.06.006. To uninstall 24.06.006 completely, upgrade to 24.06.007 and then uninstall. Upgrades from 24.06.006 to 24.06.007 will not take effect until after a reboot or manual restart.
Bowtie will now try two different strategies for Wireguard endpoint address lookup. This may help when switching between networks where the endpoint has a different IP address on the two networks.
24.07.006¶
Released on 18 July, 2024.
Server¶
Fixes¶
Fixed an issue that precluded the
sosdaemon from starting directly in some cases.Some control plane API routes have been restricted to logged-in users only.
Features¶
A new task to clean up orphaned KVS files, like downloaded network block lists, has been created. By default it runs every 4 hours.
Client¶
Features¶
Bowtie client
rpmpackages are now available for CentOS Stream. See the client setup documentation for additional information about using these new packages.
Fixes¶
Windows: handshake status now displays correctly.
24.07.005¶
Released on 16 July, 2024.
Server¶
Features¶
Typeahead search has been added for policy building and user group management.
Fixes¶
Fixed an issue on Controller
xenimages that caused errors related togrubinstallation when undergoing updates.Bowtie Controllers are now identified by their appliance name and version in ESXi environments.
Controller HTTP and HTTPS endpoints will now respond to the backend health check path (
/-net/api/v0/ok) in response to any request regardless ofHostheader.
Client¶
Fixes¶
Fixed an issue on Windows where Bowtie DNS would sometimes fail to pick up DNS server changes.
The support page now populates its status and organization detail information faster.
Windows: if Bowtie DNS fails health checks for an extended period of time, it is restarted.
24.07.004¶
Released on 10 July, 2024.
Server¶
Fixes¶
A defect has been identified under certain circumstances when adding and removing controllers via the API. This release includes a fix for a subsequent failure to boot controllers after the defect case has occurred.
24.07.003¶
Released on 9 July, 2024.
Server¶
Enhancements¶
The Controller reverse proxy software has been updated to Caddy 2.8.
Client¶
Deprecations¶
Bowtie will now only read configuration files with the extension
.confor.toml
Features¶
Bowtie will now always ensure there is a backup of the configuration file.
Fixes¶
On Windows, the light and dark mode tray icons should now look a bit nicer with some display scaling settings.
There are new mechanisms for recovering from failed states on the client. The Bowtie client now stores multiple copies of the critical information needed to operate clients on disk. In the event of data loss from disk degradation or program errors in one area, many circumstances can now be fully recovered.
Linux: if you originally installed Bowtie with a .deb package that contains a configuration file and upgrade with a .deb package that does not contain a configuration file, the configuration file will be restored from backup.
24.07.002¶
Released on 5 July, 2024.
Server¶
Features¶
A new Web GUI has shipped. Includes several new features including better live input validation in many areas. It’s also quite good looking.
Fixes¶
Controller backup and restore operations were not capturing reverse proxy material like Caddy configuration and TLS certificates. This update improves the backup service to include these services and files.
Errors in
taskexecution would sometimes cause apanic. They now are handled correctly.
Client¶
Fixes¶
Version 24.06.003 introduced DNS health checking. One endpoint/check pair was
dns-upstream-test.bowtie.workspointed at TEST-NET-3 addresses in RFC1918 space. This was found to be filtered by some DNS providers, erroneously suggesting that DNS was failing and Bowtie would refuse to install DNS. Now two addresses are checked for static upstream responses:dns9.quad9.net&dns.msftncsi.com
Features¶
On Windows, the Bowtie tray icon will now automatically change its appearance when the Windows color mode setting is changed between dark and light.
24.07.001¶
Important
This release includes important changes that administrators should review.Released on 1 July, 2024.
Server¶
Fixes¶
Updated Controllers to a patched version of
opensshto address CVE-2024-6387. The service will restart automatically on update; no further action is required after performing a Controller update.
Meta Control Plane¶
Fixes¶
Fixed a minor bug that listed some release candidate versions in the incorrect order when querying for the latest package.
24.06.003¶
Important
This release includes important changes that administrators should review.Released on 27 June, 2024.
Server¶
Fixes¶
Fixed an issue that prevented user edits from being saved.
Fixed an issue that caused the service that printed OpenSSH host keys at start time to crash when it encountered DSA keys.
Fixed an issue that would cause Grafana OAuth authentication to enter an infinite location redirect loop.
Enhancements¶
Controller SoS bundles now include additional information about configuration settings like backups and automatic updates.
The foundational operating system for Controllers has been updated from NixOS 23.11 to 24.05.
This update includes the following noteworthy version changes. If you rely on any of these packages for downstream integrations (such as observability with Grafana and Loki), ensure that the updated versions are compatible with your existing configuration (and update those configurations if necessary).
This change includes an upgrade from Linux kernel version 6.1.82 to 6.1.95. System services should continue to operate normally across kernel updates, but if you require that the system run on the newer kernel, you should follow-up with any update actions with a system reboot to run on the newer kernel, but this step is not required.
Package
Old Version
New Version
Linux kernel
6.1.82
6.1.95
cloud-init
23.1.2
23.3.3
amazon-ssm-agent3.2.1798.0
3.3.484.0
awscli22.13.33
2.15.43
cloud-init23.3.3
24.1
grafana10.2.6
10.4.4
loki2.9.6
3.0.0
openssh9.6p1
9.7p1
opentelemetry-collector-contrib0.87.0
0.101.0
prometheus2.49.1
2.52.0
promtail2.9.6
3.0.0
python3.11.8
3.11.9
tempo2.3.0
2.4.2
Client¶
Features¶
A new configuration option
auth_prompt_strategy=Neverhas been added which is appropriate for device-only authorization and multi user terminals.Adds a
local_dns_provider="NrptRulesSplitDns"which obviates “No Internet” reported issue on windows and helps connection stability in many circumstances, only sending requests to Bowtie DNS for Managed DomainsAdds a
local_dns_provider="NrptRules"which obviates “No Internet” reported issue on windows and helps connection stability in many circumstances.
Fixes¶
The wireguard interface will now be downed when a pause is requested.
We have added several checks to configuration file loading to provide more information and smoother operations if any configuration file is damaged or incomplete.
Addressed some cases where the Bowtie GUI application (tray icon) would fail to launch. It should now always launch successfully following an interactive installation.
A new state machine has been added for DNS supervision. Bowtie will only take over primary DNS if all required checks pass, and will uninstall itself if any tests fail.
24.06.002¶
Released on 21 June, 2024.
Server¶
Features¶
Controllers now support the ability to perform regularly-scheduled backups and restore from those backups either interactively or automatically. Consult the backup and restore documentation for additional information.
Client¶
Fixes¶
On Windows: At boot, awake from sleep, or certain network change events, there was a race condition between
bowtie-dnsand the network interface coming online. An upstream test was added and the service is much more resilient to network change events of any kind.Bowtie refuses to install routes that will cause conflicts with already existing system routes. This logic was too aggressive, and now Bowtie will install routes that overlap but do no conflict.
For example, if you have a system route 10.0.0.0/24 and wish to install a Bowtie route at 10.0.0.0/8 this will now work. The 10.0.0.0/24 route is more specific and the OS will preferentially route to it. The Bowtie route will not interfere with the existing system route.
A MacOS segfault introduced in 24.05.003 has been fixed.
The Bowtie installer now deletes any log files created by older versions of Bowtie that used different log file names.
Bowtie will now not switch networks from one wireguard peer to another as long as the previous peer is still up.
Features¶
On MacOS Bowtie now creates a
_bowtiesystem user and uses it to run the DNS daemon. (Linux has used thebowtieuser since 24.05.001)Wireguard handshake status added to support help page.
24.06.001¶
Released on 6 June, 2024.
Client¶
Fixes¶
A memory leak was fixed in Linux
Features¶
Four different strategies for setting Linux search domains have been added. The configuration variable
search-domains-strategymay be set to one of these 5 values:noneresolvectl: use theresolvectlCLI toolresolved-conf-d: stores search domains in/etc/systemd/resolved.conf.d/bowtie-search-domains.confnetwork-manager-conf-d: stores search domains in/etc/NetworkManager/conf.d/bowtie-search-domains.confnetwork-manager-dbus: notifies NetworkManager about the search domains using D-Bus.
24.05.005¶
Released on 31 May, 2024.
Server¶
Fixes¶
The user edit form in the administrative panel has been modified so that feedback on password requirements is shared, and errors prevent the form from closing and resetting.
Updated the version of
gitincluded on Controllers to 2.44.1 to address recent CVEs.Optimized Controller images to reduce their overall system size.
Fixes an issue in which IPv4 address allocations where not reused when already assigned to a device. If a device contains an IPv4 allocation then it’s reused and assigned appropriately.
Features¶
Controllers now bundle Zabbix agent 2. The daemon is not enabled by default and must be configured before use. Consult the related documentation for additional information.
Client¶
Features¶
The Bowtie client has gained the API endpoints:
http://localhost:17133/organizations,http://localhost:17133/organizations/:idandhttp://localhost:17133/organizations/:id/peersThe latter two endpoints support
Content-Type: text/event-streamas well asContent-Type: application/jsonThese endpoints will be used by the Bowtie client support page which is accessible via
http://localhost:17133/static/support.htmlor help in the tray menu.The help page (also available at
http://localhost:17133/static/support.html), has gained more information, including detailed information on wireguard peers.
Fixes¶
Fixed an issue where check-ins returning HTTP 204 were reporting as HTTP 400 on the status screen.
24.05.004¶
Released on 23 May, 2024.
Client¶
Fixes¶
Version 24.05.003 reported as
24.05.003-rc.6. Version 24.05.004 is being released to eliminate ambiguity between released and unreleased software. There are no functional changes between 24.05.003 and 24.05.004. Incorrect tagging affected client-reported version numbers in the devices page and API and reported version number on the support window of the tray application.
24.05.003¶
Released on 22 May, 2024.
Server¶
Features¶
Support bundles emitted from Controllers now include
iptablesdumps.
Fixes¶
The
bowtie-serverprocess on Controllers was not honoring all signals to shut down cleanly, which it now does.
Client¶
Features¶
Adds two local DNS observability feature, both accessible via the
supportpage from the tray icon. The first is adig-like resolving tool to explain private tunnel DNS modifications. The second is an upstream monitor to show what Bowtie DNS will forward to for other internet traffic. This record is pulled from your local operating system, and when that is not available fallback records can be set in your configuration file atdns_fallback_ipv4anddns_fallback_ipv6. Fallback records currently default to public DNS providers at Hurricane Electric and Verisign.Additionally DNS upstream change resolution time has been reduced from 15-30s to a median time of 1.5s for network change events on Windows. MacOS and Linux upstream resolution continues to be effectively immediate, querying the operating system on every request.
Fixes¶
DNS concierge & block lists are now disabled while Bowtie is paused.
24.05.002¶
Released on 15 May, 2024.
Server¶
Fixes¶
24.05.001 included a regression for IPv4 pools that did not persist through controller restarts. This has been resolved.
24.05.001¶
Released on 13 May, 2024.
Server¶
Features¶
IPv4 Address Pools delegated to Bowtie for assignment can be deleted, with cascading effects from the administrative web UI. They can also be deleted from the API by setting
cascade=true.tmuxis now included on all Controllers.
Fixes¶
Fixes an issue in which new IPv4 pools assigned through the web client were not assigned to the wireguard interface. Previously a controller restart was required to resolve the issue. Modifications to IPv4 pools are now effective immediately and no longer require controller intervention.
Client¶
Features¶
A compatibility mode was added to MacOS for services which scan local TLS traffic.
Fixes¶
Silent installations on Windows (including automatic updates where those are available) will now launch the Bowtie tray icon, just like interactive installs can.
On Windows, updating to a new version of Bowtie will now remove any previous versions already installed. It should no longer be possible to have more than one version of Bowtie installed at a time.
24.04.004¶
Released on 29 April, 2024.
Server¶
Enhancements¶
The control plane web interface administrative configuration section now includes the ability to change telemetry preferences.
Features¶
Support bundles (SoS diagnostics) may now be generated on Controllers exclusively via the command line instead of solely over HTTPS.
Controller SoS endpoints now support browser-based interactions into addition to plain API-based requests.
Assisted support (SoS) capabilities for Controllers are now available in the Control Plane UI on Controllers and as the
soscommand on the command line.
Client¶
Deprecations¶
The
.exeWindows package has now been fully deprecated in favor of the.msipackage.
Features¶
On MacOS and Linux, Bowtie has gained the ability to run its DNS component as a user other than root. This can be enabled by either setting the
dns_user_idsetting in the configuration file, or by creating a user namedbowtie.The .deb install package creates a
bowtieuser, so it will run DNS as a non-root user by default. The same capability exists in MacOS but it is not yet turned on by default.When you request a support bundle from the Bowtie client, that will be automatically sent to Bowtie support. You can opt-out of this behavior by setting
send_sos_to_bowtie_strategy = "OnDemand"in configuration.On Windows, Bowtie now installs two separate services, which you can see as
Bowtie ServiceandBowtie DNSin the Windows services utility. This should enable faster responses to network changes.
Fixes¶
The default for
metrics_socket_addresshas changed from the Wireguard IPv6 address to127.0.0.1:17133.On MacOS, Bowtie temporarily disables during a captive portal entry session to allow the portal to be accessed.
Windows 10 clients should no longer see the “No Internet” status reported for Internet-connected networks after e.g. resuming form standby.
The default log level for the Bowtie client has been set to
info, up fromdebug. To revert this change you can setverbose = 1in the Bowtie configuration file. Further reducing the log level tonwarncan be done withsilent = 1; toerrorwithsilent = 2.
24.04.003¶
Released on 15 April, 2024.
Client¶
Features¶
A compatibility mode was added to MacOS for services which exclusively use local private IP address resolution.
24.04.002¶
Released on 11 April, 2024.
Server¶
Fixes¶
Fixed a bug that caused errors when provisioning ACME TLS after a problematic Caddy update. TLS provisioning should be functional once more.
24.04.001¶
Released on 9 April, 2024.
Server¶
Enhancements¶
The
/grafanaController endpoint is now access-controlled via login to the Controller control plane web application. To continue accessing Grafana, please ensure that you are logged in to the Controller’s web interface.Updated the base Controller appliance operating system to reflect the latest upstream package updates.
The table below lists relevant user-facing packages that may impact custom configuration settings on deployed Controllers:
Package
Old Version
New Version
dex2.38.0
2.39.0
grafana10.2.4
10.2.6
grafana-loki2.9.4
2.9.6
linux6.1.78
6.1.82
prometheus2.49.0
2.49.1
promtail2.9.4
2.9.6
When upgrading your Controller, please bear the following release notes in mind:
This update includes an update from Linux kernel version 6.1.78 to 6.1.82. System services should continue to operate normally across kernel updates, but if you require that the system run on the newer kernel, you should follow-up with any update actions with a system reboot to run on the newer kernel, but this step is not required.
Dex has been updated from version 2.38.0 to 2.39.0. Upstream release notes include important changelogs about LDAP connectors.
At the time of writing, a scan of all operating system dependencies yielded no outstanding critical vulnerabilities requiring immediate action.
Fixes¶
Raised the default web frontend rate limit significantly to avoid spurious HTTP
429errors. This setting remains configurable if issues persist in particular environments.
24.03.007¶
Released on 29 March, 2024.
Server¶
Features¶
Controllers now support the ability to collect and deliver diagnostics bundles to Bowtie for assisted support efforts in the event of a troubleshooting situation. Data is not sent by default and explicit administrative steps are necessary to initiate the process. See the Controller SoS section for additional information.
Controller images are now available in Azure GovCloud. See the Bowtie downloads page for Azure for a list of regions including those hosted in GovCloud.
policyobjects now contain astatusfield that can be in either anenabled/disabledstate. If apolicyisdisabledit’s evaluation will be ignored.Enabledis the default status to maintain backward compatibility of the API, and existing values in the database. The UI has been been modified to allow for a user to toggle the status of one or many policies.Individual IPv4 Addresses can now be released via the API or Web GUI.
Fixes¶
Fixed an issue where the single sign-on service provider (
dex.service) would fail on Controller startup orupdatewhen no configuration files were present.
Client¶
Fixes¶
On versions prior to 24.03.007, system DNS could be broken by certain combinations of WiFi network changes and switching from wired Ethernet.
Documentation¶
Features¶
Added Windows client support for DNS search domains.
Concierge domains configured as search domains in the Bowtie server will now function as search domains on clients. This means that for instance, for concierge domain
example.comconfigured as a search domain, the nameapp1will now resolve as if the user had enteredapp1.example.com, and typing justapp1into e.g. a web browser should work as expected.Currently, this feature is only present on Windows clients.
24.03.006¶
Released on 20 March, 2024.
There are no release notes for this version.
24.03.005¶
Released on 19 March, 2024.
Client¶
Fixes¶
In windows a crash loop was observed in 24.03.004 preventing normal operation for most users. This was due to a change in our IPC passing and window handling code. The crash loop has been resolved.
Server¶
Features¶
Previously, the smallest unit of a policy destination was (“host”, “protocol”, “port”); with no way to compose arbitrary host groups. We found this to be limiting to creating narrow rule sets. We have introduced host collections to alleviate this. It is currently in an early release state and API-only. If your rule set would benefit from host collections, please reach out and watch this space.
24.03.004¶
Released on 12 March, 2024.
Server¶
Features¶
The User Groups page now allows group deletion.
Fixes¶
Navigating between tabs in the Settings page should be a smoother experience.
Fixed an issue that prevented API keys from being deleted.
A component for displaying policy resources was regularly reused. This created some confusion with which actions were available in which areas. The “Trash” icon no longer shows up on policy resources in read-only contexts.
Fixed CSS rules that were preventing some fields from displaying legibly when browsing in dark mode.
The OpenAPI spec for the Bowtie server API now contains a more complete listing of available API endpoints and associated types.
Documentation¶
Features¶
Added documentation for address pools.
Added documentation regarding how to configure and enable automatic Controller updates via the control plane web interface.
24.03.003¶
Released on 7 March, 2024.
Client¶
Fixes¶
Versions 24.02.004 through 24.03.002 of
bowtie-dnsreturned IPv4 A records for private resources that were inaccessible over IPv4 if no IPv4 addresses were configured.
24.03.002¶
Released on 6 March, 2024.
Server¶
Features¶
Controller images are now available for Xen-based hypervisors including XCP-ng. See the Bowtie download platforms page for Xen to download
.ovaappliance image files.
24.03.001¶
Released on 6 March, 2024.
Server¶
Features¶
Auto-updates per-controller can now be configured by clicking on the controller in the /control-plane view in the web GUI.
IPv4 pools with manual address assignment are now able to be assigned from the Devices page in the web GUI.
Enhancements¶
ESXi
.ovaimage default resource allocations have been adjusted to reflect recommended system requirements (4 cores and 4GB memory).
Fixes¶
Active Directory GUIDs were being ingested with inconsistent formatting. The binary representation via LDAP was different from the hex representation via OIDC. This is now repaired in the LDAP sync task.
24.02.006¶
Released on 29 February, 2024.
There are no release notes for this version.
24.02.004¶
Released on 29 February, 2024.
Server¶
Features¶
Beta policy evaluation tool in the policy area. This page is for debugging and understanding the policy engine. It will show you the current state of the policy engine, and allow you to see how it is evaluating a given request.
The DNS configuration page can now be sorted and filtered.
Controller images are now available in AWS GovCloud. See the Bowtie downloads page for AWS for a list of regions including those hosted in GovCloud.
Fixes¶
Fixed an issue that caused updated control plane web assets to be incorrectly cached, causing inconsistent behavior after updating Controllers.
A write lock was erroneously held through a read operation which did not close the transaction. Additionally an error in rolling back that transaction causes an unrecoverable panic. In some cases this cascades through the cluster. The offending operation has been repaired.
Enhancements¶
Updated the base network Controller appliance operating system to reflect the latest upstream package updates. This includes patch version updates to Grafana as well as patches to recent CVEs in packages like
glibc.This update includes an update from Linux kernel version 6.1.75 to 6.1.78. System services should continue to operate normally across kernel updates, but if you require that the system run on the newer kernel, you should follow-up with any update actions with a system reboot to run on the newer kernel, but this step is not required.
Helm Chart¶
Features¶
The Helm chart now accepts a list of environment variables to set under the
server.envkey for arbitrary settings like changingRUST_LOGtodebugwith avaluesfile like the following:server: env: - name: RUST_LOG value: debug
Fixes¶
Fixed an issue that caused the Bowtie server container to fail to emit its correct version string.
Client¶
Fixes¶
At 24.01.001 an upgrade of a dependency caused changes in behavior on MacOS which meant the Bowtie icon appeared in the task switcher and the dock. This has been resolved.
Known Issues¶
There is a known issue where the Bowtie tray application sometimes fails to start successfully on Windows. The Bowtie service will still be running, you may continue without the tray application. You can restart the tray application by searching for “Bowtie” in the windows menu, by clicking on
C:\Program Files\Bowtie\24.02.004\bin\bowtie.exeor by restarting your computer.
Features¶
When IPv4 Support is enabled on the controller for a given device, A records are no longer dropped by default. DNS Strategies are designated on the control plane, per managed name.
In prior versions, if a domain was set up with the DNS64 flag, and DNS returned an IPv4 address within a range set up with NAT64 rules, Bowtie would return 0 records for A requests and return DNS64 answers for AAAA requests.
This has been relaxed. Now, in the above scenario if the IPv4 address is routable, the A record response is not squashed.
When IPv4 Support is enabled on the controller for a given device, A records are no longer dropped by default. DNS Strategies are designated on the control plane, per managed name.
Bowtie now refuses to install IPv4 routes that conflict with local system routes.
For instance, if you have a Bowtie site with a 192.168.4.0/22 network and you use it on a computer that is connected to a 192.168.4.0/22 network, Bowtie will not install routes to the Bowtie 192.168.0.0/22 network to ensure that it does not break local connectivity.
This also applies when the Bowtie network length is shorter than the local network. If the Bowtie site is 192.168.4.0/22 and the local network is 192.168.0.0/20 Bowtie will not install routes the Bowtie 192.168.0.0/22 to ensure that it does not break local connectivity.
Operating systems preferentially route to the most specific network so if the Bowtie site has a network length longer than the local network, Bowtie routes are installed. For example, if the Bowtie site is 192.168.4.0/22 and the local network is 192.168.5.0/24, Bowtie will install routes for 192.168.4.0/22. The operating system will route 192.168.5.0/24 to the local network, but the rest of the Bowtie network will be accessible.
Servers located on the Bowtie site network can be accessed via NAT64 if they are not accessible via IPv4.
24.02.003¶
Released on 22 February, 2024.
Server¶
Enhancements¶
In addition to native cloud images for platforms like AWS, GCP, and Azure, raw disk images for each platform are now available for use in special cases such as import into currently-unsupported regions. Consult the platform-specific documentation under the Controller installation section for more information.
Controller appliances for GCP are now available as native GCE images (in addition to raw disk image files). Note that public custom images are not listed over the GCP API and must be explicitly referenced by their resource identifiers when creating new GCE instances. Please refer to the GCP setup documentation and the GCP downloads page for additional information.
Fixes¶
Fixes an issue with policy order application.
Meta Control Plane¶
Features¶
Downloads now include buttons to copy
curlorwgetcommands to the clipboard to aid with downloading packages in command line environments.
24.02.002¶
Released on 16 February, 2024.
Server¶
Fixes¶
Previously policy order rendering silently relied on the ID of the policies as well as the “order” field. Now ordering in the policy engine and the UI is consistent with the
orderfield.Device assignment and web application flows share some authentication code. All prior versions of Bowtie were failing to expire a client side cookie for device-id which made multiple tasks (web admin + device authentication) in the same browser behave incorrectly. This has been patched to expire the device-id on any successful authentication of the
/password-loginor SSO.
Features¶
Added the ability to see user status and manually activate/deactivate users from the Web UI. This feature was previously exposed to the API only.
Client¶
Features¶
The Help page has gained more fine grained status information.
24.02.001¶
Important
This release includes important changes that administrators should review.Released on 14 February, 2024.
Server¶
Features¶
“Last Seen Version” is displayed on the
Devicespage of the web GUI.Operators may opt-in to pre-release builds of Controllers. To do so, either pass the
--prereleaseflag to theupdatecommand-line utility or set theBOWTIE_PRERELEASEenvironment variable if updating Controllers via automatic updates (for example, by including the lineBOWTIE_PRERELEASE=1in/etc/default/update).Bowtie now provides Controller network appliance images for Google Compute Engine (GCE) with EFI support.
Enhancements¶
The foundational operating system for Controllers has been updated from NixOS 23.05 to 23.11.
This update includes the following noteworthy version changes. If you rely on any of these packages for downstream integrations (such as observability metrics from
opentelemetry-collector-contrib), ensure that the updated versions are compatible with your existing configuration (and update those configurations if necessary).Package
Old Version
New Version
Linux kernel
6.1.38
6.1.75
cloud-init
23.1.2
23.3.3
grafana9.x
10.x
jq1.6
1.7
loki2.8.6
2.9.4
openssh9.3p2
9.5p1
opentelemetry-collector-contrib0.77.0
0.87.0
prometheus2.44.0
2.49.0
prometheusnode_exporter1.5.0
1.7.0
promtail2.8.6
2.9.4
python3.10.13
3.11.6
tempo2.1.1
2.3.0
Fixes¶
Fixed some additional cases in which the
bowtie-serverprocess would crash when restarting, causing server daemon instability.
Client¶
Features¶
On MacOS, Bowtie has gained the ability to auto-select the DNS port. If the configuration parameter
local_dns_listen_portis set to0, the port will be auto-selected. Port 53 will be chosen if it is available, otherwise a random port will be chosen. If a port other than 53 is selected manually or automatically, the MacOS firewall (pf) will be used to direct DNS traffic from port 53 to the chosen port.The default for
local_dns_listen_porthas been changed to 0. Setlocal_dns_listen_portto 53 to fail instead of using a firewall redirect if port 53 is unavailable.Bowtie on MacOS has gained the ability to operate on a port other than the standard DNS port of 53. To change ports, set the
local_dns_listen_portoption to an otherwise unused port in the configuration file in/etc/bowtie/configuration/.When this option is set to a value different than 53, Bowtie installs some pf firewall rules to redirect DNS queries from port 53 to the new port.
Some of the applications that can claim port 53 and cause Bowtie to fail are Cirrus Labs’ Tart VM, old versions of Docker and the Internet Sharing facility of MacOS.
Fixes¶
The Default MTU for the VPN tunnel has been changed to 1280 on MacOS, matching the previous behavior on Linux.
24.01.004¶
Released on 1 February, 2024.
Server¶
Features¶
Resource groups can now be deleted from the UI instead of just the API. Resource groups still in-use by policies are protected in the API.
24.01.003¶
Released on 31 January, 2024.
There are no release notes for this version.
24.01.002¶
Released on 30 January, 2024.
Server¶
Features¶
Controller images compatible with ESXi VMWare hypervisor environments are now available as
.ovadownloads.
Client¶
Fixes¶
Updated the Bowtie client UI framework that includes fixes for crashes that occurred on MacOS x86 platforms.
MacOS: fix for log directory permissions issue that prevented tray app from starting for some
24.01.001¶
Released on 25 January, 2024.
Server¶
Features¶
Controller events like updates are now recorded and displayed under the System Messages page of the control plane interface. Release notes are also provided on this page to quickly summarize changes. Consult the user documentation for additional information.
Individual resources may now be deleted when managing policies in the Control Plane web interface.
Added ability to force device re-authentication after
Nnumber of minutes. Off by default. Go to the/settingspage or update the org configuration API to activate.
Client¶
Deprecations¶
On Windows, the option
--local-dns-provider(akalocal_dns_providerin configuration files), the default valuenet-powershell(akaNetPowershell) has been renamed toregistry-injector(akaRegistryInjector).On MacOS the option
--wireguard-provider=boringtun-hybrid(wireguard_provider="BoringtunHybrid") is now gone. Use--wireguard-provider=boringtun(wireguard_provider="Boringtun") and--routing-provider=route-cli(routing_provider="RouteCli") instead. These are the defaults and recommended, so alternatively the CLI arguments or configuration file options may be removed. All the other wireguard providers (wireguard-go,boringtun,boringtun-cli) are still available and now gain the ability to specify a different routing provider.On MacOS the alternative routing provider is
--routing-provider=route-socket(routing_provider=RouteSocket). This provider currently is in an alpha state, has known issues and is not recommended.
Features¶
bowtie-servicehas gained the option--dry-run(dry_run = truein configuration files). If set,bowtie-servicewill log the commands it would at the INFO level rather than actually run them. See –verbose/–silent for more information on log levels.This is only effective for providers that use command line commands. On MacOS, the default
boringtunprovider does not use command line commands.--dry-runshould be coupled with--wireguard-provider=wireguard-goor--wireguard-provider=boringtun-cli.A new button was added to the “Help” screen in the Bowtie tray application to trigger collection of Bowtie logs and diagnostic information. This creates a zip or tar file that can be then sent in to assist support.
On MacOS or Linux, this diagnostic file may be generated manually by running
bowtie-ctl inspect.Linux clients have gained the option
dns_supervisor, (--dns-supervisoron the command line). The default value isSystemd, the old behavior may be obtained through the valueBowtieService.The main functional difference between these two options is that the
bowtie-dnslogs are separated into thebowtie-dnsjournal with theSystemdoption, rather than appearing in thebowtie-servicejournal.Behind the scenes the
Systemdoption creates abowtie-dnssystemdservice, andbowtie-servicestarts and stops this new service when appropriate. WithBowtieServiceas the option,bowtie-dnsis forked frombowtie-service.The OS-specific Wireguard providers have been split into two separate Wireguard and routing providers. This is provided by the new command line option
--routing-provider(routing_providerin configuration files) in addition to the previous option--wireguard-provider(wireguard_provider).
Documentation¶
Features¶
JSON-formatted changelogs are now available on the user documentation site under the
/changelog.jsonURL.Release notes and changelogs are now available as feeds from the user documentation site. See the documentation for additional information.
23.12.003¶
Released on 13 December, 2023.
There are no release notes for this version.
23.12.002¶
Released on 13 December, 2023.
Server¶
Fixes¶
Fixes a bug in DNS Block Lists where tasks were not automatically created when sending a URL and also an empty
contentsblock.
23.12.001¶
Released on 6 December, 2023.
Server¶
Enhancements¶
Updates the base operating system packages to reflect the latest upstream changes. This includes non-breaking changes for security fixes in packages for Loki and Promtail and openssl 3.
This update includes an update from Linux kernel version 6.1.38 to 6.1.62. System services should continue to operate normally across kernel updates, but if you require that the system run on the newer kernel, you should follow-up with any update actions with a system reboot to run on the newer kernel.
Fixes¶
Fixed an issue in which a call to
updatea Controller (via either interactive shell or automatic timer) could hang indefinitely whencloud-initfails to complete.Several improvements to DNS block lists:
Remote upstream URLs are now retrieved asynchronously in the background on update. This should result in much faster changes when updating DNS block lists.
DNS block list update tasks will remove themselves when their accompanying DNS block list resources are deleted.
DNS block list meta update tasks will remove themselves when no DNS block lists are defined and the meta update task is no longer necessary.
Fixed an issue in which the
bowtie-serverservice failed to log a correct version string when starting.
Features¶
Added a flag to optionally disable the
Secureoption when sendingSet-Cookieheaders in development. This flag should not be set in production environments. Consultbowtie-server --helpfor usage.
Client¶
Features¶
Added support for connecting to multiple organizations simultaneously.
To use this feature, place one or more configuration files with an
entrypointline in the Bowtie configuration directory (on MacOS and Linux/etc/bowtie/configuration, and on Windows,C:\ProgramData\bowtie\configuration).For example, the following snippet shows a client configuration on Linux that will connect to two organizations with two separate controllers:
$ cat /etc/bowtie/configuration/first.conf entrypoint = [ "https://controller.example.com" ] $ cat /etc/bowtie/configuration/second.conf entrypoint = [ "https://controller.rock.associates" ]
Bowtie currently only supports DNS on a single organization at a time. To switch to a different organization, access the “pause” capability by right-clicking the Bowtie system tray icon.
On MacOS, logs are now sent to the system’s unified log service rather than being stored in files.
Logs may be accessed by using
bowtie-ctl inspect, by using the MacOS console app or by using thelogcommand:log stream --info --debug --predicate 'subsystem = "works.bowtie.bowtie-service"'
A subsystem predicate of
works.bowtie.bowtiewill dump the logs from the tray application rather than the service.Added the ability to pause and resume a Bowtie connection. This may be accessed by right clicking on the Bowtie tray application and selecting “pause” or “resume”. These menu items are only respectively available if the connection is in the “Connected” or “Paused” state.
Fixes¶
Fixed an issue which prevented the tray application from running for multiple users simultaneously.
Enhancements¶
The
.msifile now includes required dependencies for Windows 10 and above. The use of theexeis not recommended for most cases.
Documentation¶
Enhancements¶
The client setup and usage documentation has been overhauled to provide complete instructions for installation, uninstall steps, and desktop application use.
Added screenshots and examples for client tray menus that include multiple organizations and pause/resume buttons.
The control plane documentation has been expanded to cover all of the administrative web pages available on Controllers.
Updated the Terraform knowledge base section to include examples illustrating how to provision
bowtie_dns_block_listresources.Updated the section about Terraform provider ordering to reflect updated capabilities of the native provider to authenticate lazily.
23.11.003¶
Released on 15 November, 2023.
Server¶
Fixes¶
Updated the
open-vm-toolspackage on VMWare Controller images to patch for the following CVEs:CVE-2023-34058
CVE-2023-34058
Features¶
policyobjects now allow an optionalorderattribute to be added and the UI supports drag and drop ordering.orderis not absolute and duplicates are allowed in the API. The web interface will attempt to rectify ordering into a linear fashion if given the opportunity. In order to preserve current behavior, existing ordering is matched upon upgrading to this version.
Client¶
Features¶
Names may be queried with
ip-orip.notation to get their Bowtie equivalent addresses and routes.❯ dig AAAA ip.172.16.1.1 ; <<>> DiG 9.18.18-0ubuntu0.22.04.1-Ubuntu <<>> AAAA ip.172.16.1.1 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 31800 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 65494 ;; QUESTION SECTION: ;ip.172.16.1.1. IN AAAA ;; ANSWER SECTION: ip.172.16.1.1. 60 IN AAAA fdc3:cbe8:ded7:7ad0:0:64:ac10:101 ;; Query time: 4 msec ;; SERVER: 127.0.0.53#53(127.0.0.53) (UDP) ;; WHEN: Thu Nov 09 17:18:42 PST 2023 ;; MSG SIZE rcvd: 70
23.11.002¶
Released on 6 November, 2023.
Server¶
Features¶
The
cloud-initexecutable is now included in the global system$PATHfor any images that support cloud-init.Hosts can now be blocked from the client en-masse via DNS block lists. Block lists can be manually curated or regularly pulled from a plain text file over
httporhttps.If groups are passed in from SSO via the
groupsattribute, they will be parsed and applied to the user.Adds the ability to set configuration options on the control plane.
GETandPOSTagainst/-net/api/v0/organization/configcan influence control plane operations such as the following:If a user successfully authenticates after installing a Bowtie client, automatically approve the device.
allow_device_approval_on_user_auth: bool
If a controller has a PSK, automatically approve it’s joining the control plane.
allow_controller_approval_with_psk_only: bool
These new options are configurable over the web interface under the “Settings” section in the navigation bar.
Documentation¶
Enhancements¶
Added some important information about how Bowtie Controllers automatically provision SSL/TLS with ACME providers. If you leverage ACME heavily in your organization and may be subject to rate limits or make use of alternative validation schemes like
tls-alpn-01, you may want to consult the updated section on ACME caveats.The documentation outlining how to use
cloud-initand leveraging it for automated setup has been overhauled to include additional documentation for theskip-gui-initfile and PSK parameter.
Features¶
Added documentation outlining how to use the Bowtie Terraform provider.
23.11.001¶
Released on 1 November, 2023.
Server¶
Fixes¶
Fixed an issue in which cloud-init hostnames were not properly ingested by some system services which could impact web endpoints functioning correctly.
23.10.012¶
Released on 31 October, 2023.
Server¶
Features¶
Added the ability to initialize the first users from cloud init.
If you create a file in cloud init at
/var/lib/bowtie/init-userswith email addresses and argon2 hashed passwords, those users will be granted administrative rights at first boot.To generate the hash for password “hunter 2” you would use this command:
echo -n "hunter2" | argon2 $(uuidgen) -i -t 3 -p 1 -m 12 -e
And then put the contents into this file
issac@example.com:$argon2i$v=19$m=4096,t=3,p=1$ZDhmOTB..........
Fixes¶
Fixed an issue where a joining controller does not fully clean up before initializing in the cluster and becomes unbootable without manual intervention
Documentation¶
Features¶
Added an example of how to reset Caddy to stock defaults in the knowledge base documentation.
23.10.011¶
Released on 30 October, 2023.
There are no release notes for this version.
23.10.010¶
Released on 30 October, 2023.
Helm Chart¶
Features¶
The image names for both the
serverandfrontendcontainers is now exposed as a top-level values parameter.Their defaults remain the same:
server: image: bowtie-server frontend: image: bowtie-assets
Fixes¶
Fixed an issue in which pre-release Helm charts referenced an incorrect image name.
23.10.009¶
Released on 25 October, 2023.
Meta Control Plane¶
Fixes¶
Fixed an issue with honoring per-user
keytokens when using the/latest/API endpoints.
Server¶
Features¶
Added the ability to use API keys to manage device acceptance.
To Create an API key you must be an
OwnerorFull AdministratorUser.Create a new API Key in the GUI or at
/-net/api/v0/api_keysKeep the key and ID.
ID: d973d102-8ae5-4c5f-b393-4302abbc5024 KEY: bts1_b6a91c33-08a3-4069-a69c-c86feda404b1
Now you can use it to get devices or set their allowed state
curl -H 'Authorization: Basic ZDk3M2QxMDItOGFlNS00YzVmLWIzOTMtNDMwMmFiYmM1MDI0OmJ0czFfYjZhOTFjMzMtMDhhMy00MDY5LWE2OWMtYzg2ZmVkYTQwNGIx' https://controller.example.com/-net/api/v0/device
Or More simply
curl -u d973d102-8ae5-4c5f-b393-4302abbc5024:bts1_b6a91c33-08a3-4069-a69c-c86feda404b1 https://controller.example.com/-net/api/v0/device curl -u d973d102-8ae5-4c5f-b393-4302abbc5024:bts1_b6a91c33-08a3-4069-a69c-c86feda404b1 \ -H "Content-Type: application/json" \ -d "{"devices": [{"id": "fd2d3981-d82e-406b-a953-35e9ce6dd39b", "state": "rejected"}]}" \ https://controller.example.com/-net/api/v0/device/state \
Fixes¶
Fixed an issue in which the
bowtie-serveraddress binding might have caused traffic sent to containers to be dropped. This option is now configurable and has been fixed in the Bowtie Helm chart.
Documentation¶
Features¶
Added release notes for software releases, providing additional context for updates. These are visible on the release notes documentation page.
23.10.008¶
Released on 20 October, 2023.
Server¶
Fixes¶
The
bowtie-serverservice now restarts in all cases, not just when exiting with a non-zero status code.
23.10.007¶
Released on 20 October, 2023.
Server¶
Features¶
A new flag called
BOWTIE_ORG_RESPONSE_BEHAVIORhas been added that controls how the Controller API will respond to API calls against the/organizationendpoint. In a future release, the/organizationendpoint will only return content for accepted devices, and settingBOWTIE_ORG_RESPONSE_BEHAVIOR=accepted-devices-onlywill preview this behavior that will eventually become the default mode of operation. Existing installations will retain the current behavior – this flag is meant as an aid in preparing operators for future changes to Controller defaults.To prepare for the new future default behavior, operators should set this variable for existing Controllers in preparation for the default to change. For example, on existing Controllers or as a bootstrapping step in cloud-init user data, creating a file like
/etc/bowtie-server.d/org-response.confthat includesBOWTIE_ORG_RESPONSE_BEHAVIOR=accepted-devices-onlywill enable the behavior.
23.10.006¶
Released on 18 October, 2023.
There are no release notes for this version.
23.10.005¶
Released on 18 October, 2023.
Server¶
Fixes¶
Some Grafana authentication settings have been made more secure by default.
23.10.004¶
Released on 17 October, 2023.
Server¶
Features¶
Added a new Prometheus exporter for use in observability collection and dashboards for wireguard. The following screenshot demonstrates the type of data available for use, including wireguard interface network traffic and last-seen timestamps for wireguard peers.
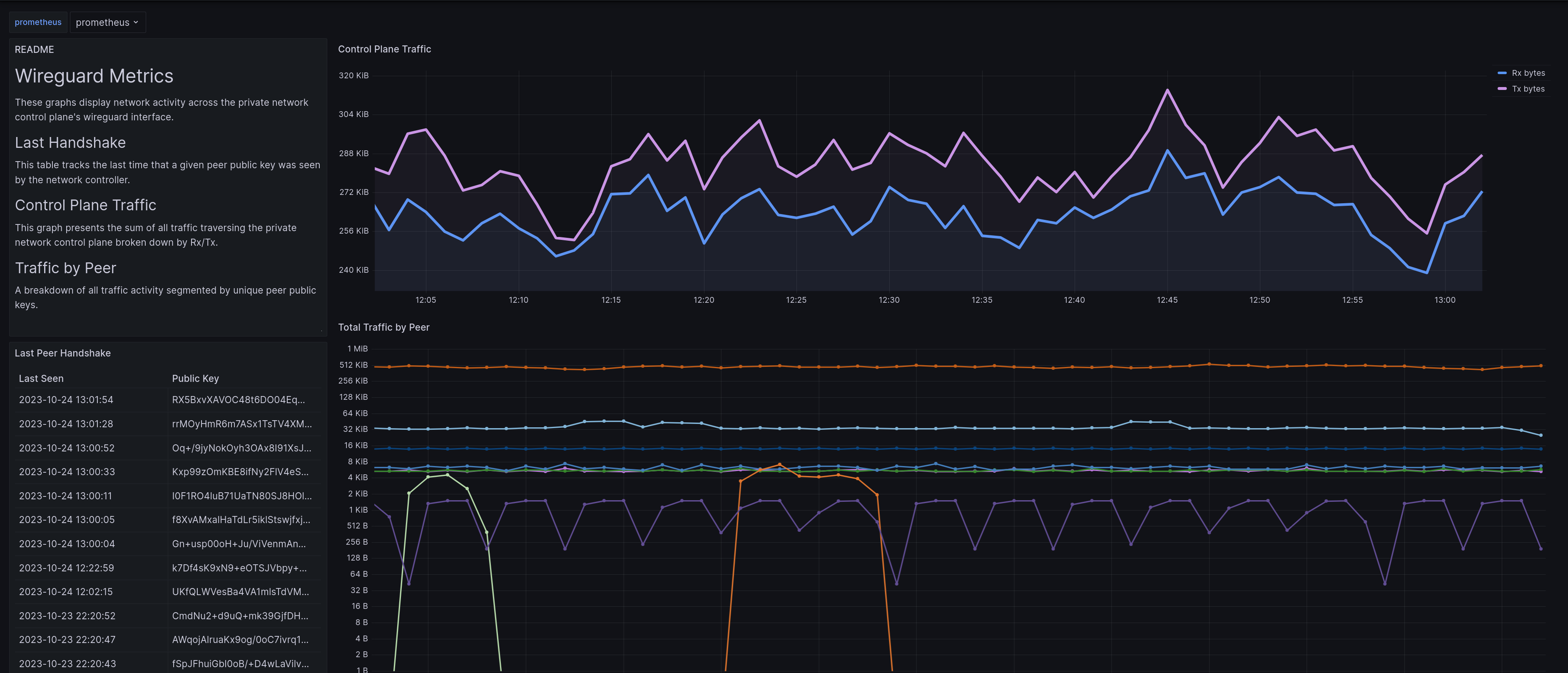
Default wireguard dashboards in Grafana¶
23.10.003¶
Released on 16 October, 2023.
There are no release notes for this version.
23.10.002¶
Released on 6 October, 2023.
There are no release notes for this version.
23.10.001¶
Released on 6 October, 2023.
There are no release notes for this version.
23.09.001¶
Released on 19 September, 2023.
There are no release notes for this version.
23.08.021¶
Released on 30 August, 2023.
There are no release notes for this version.
23.08.020¶
Released on 28 August, 2023.
There are no release notes for this version.
23.08.019¶
Released on 26 August, 2023.
There are no release notes for this version.
23.08.018¶
Released on 25 August, 2023.
There are no release notes for this version.
23.08.017¶
Released on 25 August, 2023.
There are no release notes for this version.
23.08.016¶
Released on 25 August, 2023.
There are no release notes for this version.
23.08.015¶
Released on 25 August, 2023.
There are no release notes for this version.
23.08.014¶
Released on 24 August, 2023.
There are no release notes for this version.
23.08.013¶
Released on 21 August, 2023.
There are no release notes for this version.
23.08.012¶
Released on 17 August, 2023.
There are no release notes for this version.
23.08.011¶
Released on 16 August, 2023.
There are no release notes for this version.
23.08.010¶
Released on 15 August, 2023.
There are no release notes for this version.
23.08.009¶
Released on 14 August, 2023.
There are no release notes for this version.
23.08.008¶
Released on 11 August, 2023.
There are no release notes for this version.
23.08.007¶
Released on 10 August, 2023.
There are no release notes for this version.
23.08.006¶
Released on 9 August, 2023.
There are no release notes for this version.
23.08.005¶
Released on 8 August, 2023.
There are no release notes for this version.
23.08.004¶
Released on 4 August, 2023.
There are no release notes for this version.
23.08.003¶
Released on 4 August, 2023.
There are no release notes for this version.
23.08.001¶
Released on 3 August, 2023.
There are no release notes for this version.
23.07.006¶
Released on 31 July, 2023.
There are no release notes for this version.
23.07.005¶
Released on 25 July, 2023.
There are no release notes for this version.
23.07.004¶
Released on 20 July, 2023.
There are no release notes for this version.
23.07.003¶
Released on 12 July, 2023.
There are no release notes for this version.
23.06.009¶
Released on 29 June, 2023.
There are no release notes for this version.
23.06.008¶
Released on 28 June, 2023.
There are no release notes for this version.
23.06.007¶
Released on 28 June, 2023.
There are no release notes for this version.
23.06.006¶
Released on 26 June, 2023.
There are no release notes for this version.
23.06.005¶
Released on 25 June, 2023.
There are no release notes for this version.
23.06.004¶
Released on 25 June, 2023.
There are no release notes for this version.
23.06.003¶
Released on 22 June, 2023.
There are no release notes for this version.
23.06.002¶
Released on 21 June, 2023.
There are no release notes for this version.